- 25-Nov-2022
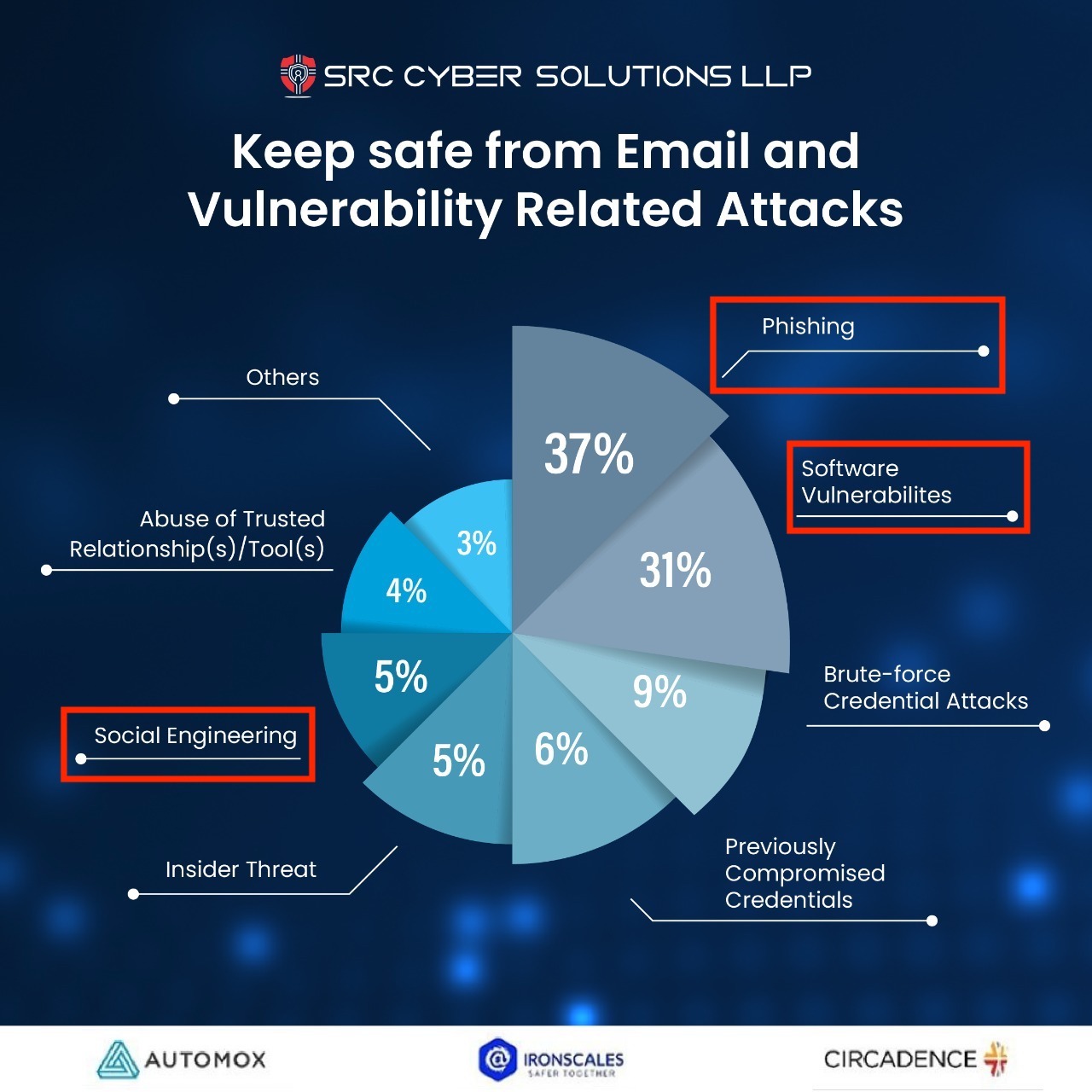
A recent report tabulated the most "Suspected Means of Initial Access" into an Organisation! #Phishing #SocialEngineering and #Vulnerabilities are the most used form of access, accounting for a shocking 72% of the cases.
A recent report tabulated the most "Suspected Means of Initial Access" into an Organisation! #Phishing #SocialEngineering and #Vulnerabilities are the most used form of access, accounting for a shocking 72% of the cases.