Blogs
Explore Comprehensive Email Security Blogs
Discover how our solutions have empowered organizations to overcome challenges, achieve operational excellence, and drive transformative growth. Learn from real-world success stories.

Love is Blind, But Your SEG Gap Analysis Shouldn't Be
Discover why traditional SEGs are failing MSPs and how modern ICES solutions can bridge the gap for better client protection and operational efficiency.
Read Blog
Why QR Codes Are Education's New Phishing Blind Spot
QR codes are everywhere in schools—and so are the phishing attacks hiding inside them. 15,000+ malicious QR codes target education daily. Here's why.
Read Blog
MSP QBRs Are Shifting to Risk Reviews and Perspective is Key
MSPs must shift QBRs from operational reviews to risk-focused discussions, aligning with client-specific compliance and security needs for 2026
Read Blog.png)
From Compromise to Control: An MSP Guide to Account Takeovers
ATOs are the new BEC. We're seeing it on our end and other companies have certainly taken notice. Attackers compromised 6.2 million customer accounts across 1,027 large organizations in 2024 according to Kasada’s 2025 Account Takeover Attack Trends Report, underscoring how routine ATO incidents have become for enterprise brands.
Read Blog
Stop Checking The Box and Switch Your SAT Perspective
Discover how to transform Security Awareness Training (SAT) from a compliance checkbox into an operational control that reduces risk, improves reporting time, and enhances business resilience for both enterprises and MSPs.
Read Blog.png)
The Phishing Renaissance, How AI Brought Back the Classics
I've been giving talks lately about the evolution of phishing attacks - tracking them from the Nigerian Prince emails of 1993 all the way to today's deepfake video calls. It's a fun trip down memory lane, filled with AOL phishing scams and QR code zebras (long story).
Read Blog
Deepfake Phishing The Next Evolution of Cyber Attacks
Check out our latest resources, expert tips, and tools to maximize your organization's cybersecurity against Deepfakes.
Read Blog
Three Security Vets Drop Uncomfortable SEG Truths
Discover what three cybersecurity leaders — SRC, IRONSCALES, and more — are saying about the biggest uncomfortable truth in digital security. A powerful insight revealed this July 2025 that every IT and business leader should know.
Read Blog.jpg)
Moving On Has Never Been So Simple: MSPs & ICES Solutions
Cyber threats are evolving, and employee awareness is key to defense. SRC Cyber Solutions offers expert-led security training, phishing simulations, and GRC solutions to build a cyber-resilient workforce.
Read Blog
Email Security Meets DMARC: A Dual Defence Against Modern Threats
Discover how combining email security with DMARC creates a powerful defense against phishing, spoofing, and domain impersonation. Enhance protection, visibility, and deliverability
Read Blog
Not Your Grandpa's Spam Filter
Spam filtering has been around forever, but let’s be honest—traditional methods haven’t exactly kept up with the times. Back in the day, IT teams leaned on static rules, blocklists, and one-size-fits-all policies to keep inboxes clean.
Read Blog
IRONSCALES Winter 2024 Update Elevates AI Capabilities to Strengthen Email Security Against Emerging Threats
Email Security Leader Introduces Advanced Features Designed to Combat AI-Driven Phishing, Strengthen Automated Defenses, and Streamline Management
Read Blog
Microsoft 365 Has an Impersonation Problem
Microsoft 365’s impersonation and spoofing controls are frustratingly bad. But you’re not alone in this struggle.
Read Blog
Building Resilience: Mastering Email Security with Gartner's Four Pillars
Email is the lifeline for the modern organization. It’s used to communicate, set meetings, share documents, discuss privileged information, shield corporate secrets, and more (both internally and externally, might I add).
Read Blog
What is IP Reputation?
IP reputation is a measure of the trustworthiness of an IP address based on its past behavior. IP reputation is important because it is used by email filters, firewalls, and other security tools to identify and block potentially malicious traffic. An IP address with a good reputation is more likely to be trusted by these tools and allowed through, while an IP address with a bad reputation may be blocked or subject to additional scrutiny.
Read Blog
Phishing for Trouble, How Simulations and Training Shape Cyber Insurance
Guess what? While you were reading this sentence, another company just fell victim to a phishing attack." No, this isn't a punchline at a cybersecurity conference...it's the somewhat alarming reality of today's business world. Phishing—the art of deception where cybercriminals masquerade as trustworthy entities to lure victims into handing over sensitive information.
Read Blog
3 Steps to Prevent Email Invoice Fraud in Your Business
Struggling with email invoice scams can be a nightmare for any business. These devious schemes threaten your company's financial health and jeopardize your reputation. You're not alone in this fight; countless companies grapple with the challenge of distinguishing between legitimate invoices and fraudulent demands for payment.
Read Blog
3 Myths of Creating Phishing Simulation Testing Campaigns
The difference between safety and a data breach often hinges on a single email. But for IT and security teams juggling numerous tasks, creating effective phishing simulation campaigns often falls by the wayside. This oversight, however, can leave your organization vulnerable to sophisticated cyber-attacks. In this post, we delve into the world of phishing simulations, uncovering why cutting corners can be counterproductive and how you can efficiently bolster your defenses. In this post, we cover 3 of the common myths surrounding phishing simulation training campaigns.
Read Blog
Navigating the Future: How Co-pilot AI is Revolutionizing Email Security
In the digital age, where email is a cornerstone of communication, particularly in the business sphere, ensuring its security is paramount. The emergence of AI-driven solutions like Co-pilot AI represents a monumental shift in the cybersecurity landscape. This article delves into how Co-pilot AI is transforming email security, offering dynamic, sophisticated solutions to counter emerging threats.
Read Blog
How AI-Based Security is a Game Changer for SMBs
If you're a cybersecurity practitioner for an SMB, you know the drill. You're often a one-person army, juggling everything from hand-wringing desktop support to updating firewalls, onboarding new employees, and dealing with the aftermath of a DDOS attack. Your days are filled with navigating MSP portals for support tickets and sifting through quarantined messages in M365 or GWS, not to mention the false alarms from well-meaning employees. It's a constant battle to do more with less.
Read Blog
Guide To Phishing Education For Employees
In today's fast-paced digital world, businesses increasingly rely on technology for their day-to-day operations, opening up many opportunities for cybercriminals to exploit vulnerabilities. Among these malicious actors,' there are many tactics, out of which phishing is one of the most pervasive and insidious threats facing organizations worldwide.
Read Blog
How Personal Phishing Attacks Compromise Corporate Security
The line between personal and professional life is increasingly blurred, especially when it comes to the use of work devices. While most employees are vigilant about corporate emails, there's a tendency to let the guard down when it comes to personal inboxes. Here's why IT and Security admins need to be just as concerned about phishing attacks sent to personal email accounts.
Read Blog
The Evolution of Phishing and AI Impacted Email Security as BEC attacks surged by 43.3%, resulting in $2.7 billion in 2022 losses, prompting 9 out of 10 organizations to adopt AI-driven defenses against sophisticated cyber threats.
Email security is often a cat-and-mouse game where cybercriminals utilize new phishing technologies and techniques to expose vulnerabilities and avoid detection—and 2023 was no different.
Read Blog
Strategic Moves in Cybersecurity Landscape. The Power of Phishing Simulation
Let's touch on a topic that IT/Security admins can't afford to overlook—phishing simulation testing.
Read Blog
Email Security in the Era of AI-Driven Threats
Artificial Intelligence (AI) has become a technology centre point across every industry now a days. But, some “AI powered” features are tactics than the real game.
Read Blog
SRC's Guide to anti-phishing tools
Phishing is a social engineering technique that aims to trick the victim into providing sensitive information or performing some action on behalf of an attacker. Phishing attacks use different communication media—such as emails, phone calls, text messages, or social media—and the impact of these attacks can be devastating to any company.
Read Blog
Phishing Insights: How The War in Israel is Fueling New Email Threats
It’s no secret that cybercriminals leverage current events and holidays to mask their phishing attempts, create urgency, and improve their chances of a successful attack.
Read Blog
AI in Email Security: 5-Things from a Seasoned Perspective on the Evolving Landscape
In my two decades of working in product management and marketing for various cybersecurity technologies, I've had the privilege of engaging with hundreds of real-world practitioners.
Read Blog
Why Microsoft Built-In Security Like Defender Is Not Enough to Stop BEC
Business email compromise (BEC) is one of the most costly and damaging types of email threats, as it relies on social engineering, deception and impersonation to defraud the recipient.
Read Blog
What is CEO Fraud?
These well-planned attacks are specifically selected, coordinated, and socially engineered to appear as if the emails come directly from a corporate executive, such as the CEO, CFO, CIO, or other VIP.
Read Blog
Safeguarding Your Organization from QR Code Phishing
In the ever-evolving world of cyber threats, threat actors are constantly finding new ways to exploit vulnerabilities and trick individuals and organizations into divulging sensitive information.
Read Blog
The top new cybersecurity products at Black Hat USA 2023
Here are the top cybersecurity tools, platforms, capabilities, services, and technologies launched at Black Hat USA 2023 that you need to know about.
Read Blog
Searching for Emails in Comprehensive Email Security and Beyond
In the Email Security dashboard, there are multiple ways to see whether the system has taken an action on an email.
Read Blog
What is Brute Force Attack
Brute force attacks pose a significant threat to information security, as they aim to gain unauthorized access to user accounts, encrypted data, and other protected systems. This article will give you an in-depth explanation of brute force attacks, their techniques, associated risks, and methods for prevention, with reference to TechTarget's definition of brute force cracking.
Read Blog
From Vulnerable to Vigilant: The Significance of Training in Phishing Prevention
In today's digital landscape, the threat of phishing attacks continues to rise, affecting organizations of all sizes. Cybercriminals are employing increasingly sophisticated methods, including the use of AI, to deceive individuals – and they are working.
Read Blog
Artificial Intelligence in cyber Security
AI in cybersecurity involves the application of artificial intelligence and machine learning algorithms to analyze vast amounts of data, detect patterns, and identify potential security threats in real-time, enabling organizations to defend against cyber attacks and mitigate risks proactively. It allows automated incident response, behavioral analysis, and adaptive defense mechanisms to protect sensitive information and strengthen overall cybersecurity posture.
Read Blog
"Presumed Safe" Emails
We're happy to announce the release of Presumed Safe emails. This capability provides privileged users with access to those emails that have been presumed to be safe by IRONSCALES' AI and Machine Learning models. IRONSCALES inspects every single email that enters your organization's mailboxes, but has traditionally provided documentation and forensics for emails that had raised suspicion of malicious intent, including emails that did or did not have an incident. With Presumed Safe, you now have full IRONSCALES coverage of all emails in the system, allowing you to gain insights into your entire email security posture and status.
Read Blog
Best Practices to Defend Against Barrel Phishing
Barrel phishing or “double-barreled phishing” is a form of spear phishing where the attacker sends several (benign) emails to the victim to gain the victim’s trust before making a malicious request. Unlike traditional spear phishing or whaling attacks, which send a single email to the victim, the attacker first “invests” in establishing a relationship with the victim to build trust and lower his or her guard before sending the actual malicious email. This requires patience from the attacker’s side and research on the victim before making an approach.
Read Blog
We Revolutionizes Email Security with Powerful New Generative AI Capabilities
IRONSCALES, the leading enterprise cloud email security platform protecting more than 10,000 global organizations worldwide, today announced the Beta launch of Themis Co-pilot for Microsoft Outlook, a GPT-powered chat assistant for self-service threat reporting. Powering Themis Co-pilot is PhishLLM, a cutting-edge large language model (LLM) hosted within the IRONSCALES infrastructure, which is the first in the IRONSCALES suite of generative AI apps for email security. The announcement comes at a time when rates of BEC and other advanced phishing attacks are climbing exponentially as they expose vulnerabilities in traditional email security solutions with social engineering tactics. A recent report from Osterman Research revealed that large organizations are expecting a 43% increase in BEC attacks in the next 12 months. In addition, cybercriminals specifically target the human element as it offers a convenient means of gaining unauthorized access to sensitive information, with phishing being one of their primary tactics. According to the 2023 Verizon Data Breach Investigations Report (DBIR), 74% of breaches involved a human element. To combat the exponential rise in phishing, Themis Co-pilot, the first in a suite of generative AI apps, was designed to empower humans to be a critical cybersecurity defense. Built on top of PhishLLM, a proprietary, patent-pending large language model, these ground-breaking capabilities will allow enterprises to become more cyber resilient by enabling end-users, regardless of role, skill, or level, to detect
Read Blog
Phishing Prevention Best Practices
According to an Osterman Research report, phishing has worsened for most organizations. With the increasing sophistication of cybercrime gangs and the complexity of modern IT infrastructure, this should be no surprise. Fortunately, an entire anti-phishing ecosystem has developed to arm security engineers and IT administrators with tools for combatting the onslaught of phishing threats.
Read Blog
How Adaptive AI Can Defend Against Zero-day Phishing Attacks
The phishing landscape is morphing rapidly. Cybercriminals are devising various attacks leveraging new tactics and technology to evade traditional, rule-based email security solutions and static-AI phishing detection tools. These tactics not only result in an increase in phishing threats but also create a lot of distraction for the security teams remediating the threats.
Read Blog
5 Steps to Running an Effective Phishing Simulation Training Campaign
Phishing simulation campaigns are vital for businesses to test their employee's security awareness and ability to help protect against cyber threats. As cyber threats become more sophisticated and malicious, companies need to stay ahead of the threats and prepare their staff to recognize phishing attacks they may encounter.
Read Blog
How To Use AI and Human Insights to Protect From Advanced Phishing Threats
Phishing has been a constant threat in cybersecurity, and as technology evolves, so do the tactics employed by cybercriminals. Advanced phishing threats have become increasingly sophisticated, making it more challenging for organizations to detect and thwart them. This post explores how artificial intelligence (AI) and human insights can be combined to effectively defend against advanced phishing threats and enhance your organization's security posture.
Read Blog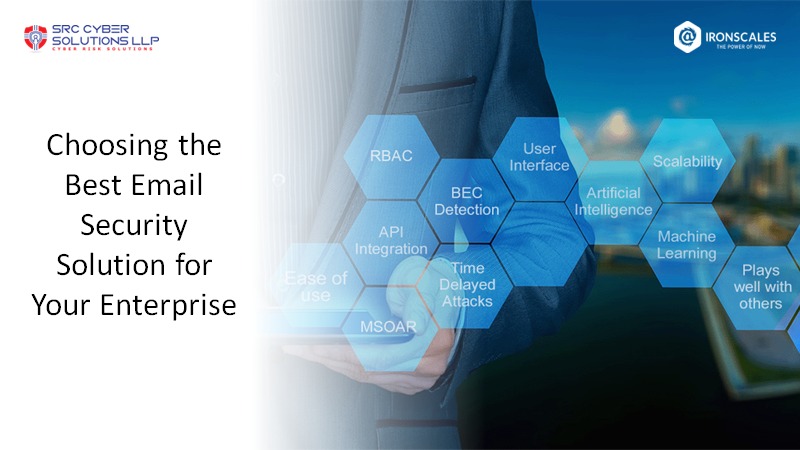
Choosing the Best Email Security Solution for Your Enterprise
Let’s get straight to the point, email-based attacks present a serious security threat for organizations today, especially enterprises. In 2022, Verizon’s Data Breach Investigations Report found that phishing continued to be one of the top three attack vectors attributed to data breaches. And during the 2020 COVID-19 quarantine, phishing attacks increased by 350%.
Read Blog
Protecting Your Organization from BEC Payroll Diversion Scams
What is BEC Payroll Diversion? Payroll diversion is a type of business email compromise (BEC) attack that occurs when a scammer successfully manipulates payroll credentials in order to defer direct deposit payments to a fraudulent account. While vulnerabilities in payroll software pose a risk, the most common method for scammers is to use social engineering and business email compromise (BEC) tactics to impersonate employees, HR and finance departments, and payroll vendors. These payroll scams have become a top lure for attackers, as the payoff is substantial.
Read Blog
The Case Against URL Rewriting For Email Security
URL Rewriting, a service used to sandbox and defang malicious URLs by sending users to a portal that displays the URL in the sandboxed environment, has many well-known weaknesses and a few that may not be obvious.
Read Blog
BEC Attacks: The Looming Threat to Large Enterprises
“Large organizations (with 10,000 or more employees) anticipate a 43.3% increase in the threat of BEC attacks in the next 12 months.” That’s just one of the many interesting data points from the new Osterman Research whitepaper, Defending the Enterprise: The Latest Trends and Tactics in BEC Attacks, that we sponsored.
Read Blog
AI and HI: Findings from the 2023 Gartner Market Guide for Email Security
Last month, Gartner published their findings and recommendations from 1,500+ customer interactions in the 2023 Gartner Market Guide for Email Security. The bad news is that despite the technology in place, the phishing problem is only getting worse as attackers evolve their strategies to avoid detection. The good news is that Gartner provides some strong recommendations to help protect organizations from these emerging threats.
Read Blog
The role of human insight in AI-based cybersecurity
To unleash the power of AI, it’s essential to integrate some human input. The technical term is Reinforcement Learning from Human Feedback (RLHF): a machine-learning technique that uses human feedback to train and improve the accuracy of an AI model.
Read Blog
The Reason Microsoft Defender Alone Isn't Enough For Modern Email Security
While Microsoft Defender can provide some protection, relying solely on it as the only layer of defense is not enough.
Read Blog
Using AI and Human Insights to Combat Advanced Phishing Threats
While 90% of all cyber breaches originate from phishing emails, traditional anti-phishing solutions have done a poor job of preventing advanced attacks. Cybercriminals have evolved tactics and leveraged new technology to launch successful campaigns and avoid detection on these legacy solutions. As phishing attacks increase in quality, quantity, and quickness of delivery, organizations need to adopt a modernized defense-in-depth strategy that combines technology and human insights to combat advanced phishing attacks like BEC, ATO, and VIP impersonation.
Read Blog
Enters 2023 Riding Significant Wave of Positive Momentum
Propelled by 58% revenue growth, multiple product advancements, and ample analyst recognition in 2022, the email security innovator is poised to reach even greater heights in the year ahead
Read Blog
Top BEC Scams and How to Protect Your Business
The phishing problem isn’t going away anytime soon. In reality, it’s getting worse as attackers adopt new tools and strategies to bypass traditional tools and coax their victims into responding to the attack. One of the most prevalent and profitable phishing attacks is Business Email Compromise (BEC) threats. In BEC scams, the threat actors pose as a vendor or high-level executive either by mimicking or gaining access to a genuine email account to build trust and get the victim to transfer funds or sensitive data.
Read Blog
Email Security Platform
IRONSCALES is an exceptional solution to prevent phishing attacks due to the strength of Themis, it's AI-powered email security platform.
Read Blog
Why Is ChatGPT a Potentially Dangerous Tool For Cybercriminals?
ChatGPT is a powerful machine learning-based text generation tool that can generate highly sophisticated and realistic text, making it a dangerous tool for criminals writing phishing emails. The emails generated by this tool can be difficult for traditional phishing detection systems to detect.
Read Blog
Why Email Security is Critical for Protecting Local Government Data
State and local government agencies store, utilize, and send massive amounts of sensitive information on a daily basis. When handling data such as personal and financial records and other significant documents that help keep these local governments running efficiently, cybersecurity is critical. One element of protecting government data is strengthening the agency’s email security.
Read Blog
Email Security Predictions For 2023
As we look ahead to 2023, it's clear that artificial intelligence (AI) will continue to shape the cybersecurity landscape, especially when it comes to phishing. Advancements in AI technology, such as the availability of ChatGPT and similar offerings, will enable attackers to launch more sophisticated and targeted attacks. At the same time, security vendors will work to develop new detection methods to counter these threats. In this article, we'll explore seven predictions for how AI will impact cybersecurity in the coming year.
Read Blog
CFOs: Reduce Financial Risks of BEC Attacks in 3 Steps
The CFO’s role in cybersecurity is often overlooked. Yet, they can be a vital partner with a CISO in risk management to protect the financial security of an organization and maximize return on investments—including investments in cybersecurity. These two leaders should collaborate to create metrics that the C-suite can comprehend to evaluate which security investments are effective, not being utilized enough, or unnecessary.
Read Blog
5 Steps to Running an Effective Phishing Simulation Training Campaign
Phishing simulation campaigns are vital for businesses to test their employee's security awareness and ability to help protect against cyber threats. As cyber threats become more sophisticated and malicious, companies need to stay ahead of the threats and prepare their staff to recognize phishing attacks they may encounter. This post provides tips for running an effective phishing simulation training campaign.
Read Blog
The Rise of Collaboration for Proactive Phishing Defense
The cybersecurity industry has been talking about collaborative approaches forever. In fact, the cyber community has been using a collaborative approach for a long time on things like the identification of vulnerabilities. It’s how CVEs are identified, verified, enumerated, and cataloged. But that’s mostly rear-looking, not real-time, not a proactive defense.
Read Blog
What Phishing Trends Await Security and IT Teams
Phishing attacks are surging. As a result, threat actors are quickly evolving their tactics to bypass legacy systems and deceive vulnerable targets, causing IT and Security teams to spend more time and money responding to threats across new attack surfaces. Unfortunately, according to the Osterman Research report, The Business Cost of Phishing, “Most organizations anticipate that Phishing threats will get work, and many would like to be better equipped to deal with it.”
Read Blog
Are Threat Actors Using QR Codes in Phishing Attacks?
Threat actors constantly tweak and refine their tactics in an attempt to evade detection or become more efficient at achieving malicious goals. Often, these tactical adjustments exploit societal changes—a pertinent recent example was the increase in phishing emails targeting remote employees.
Read Blog
What Phishing Threats Are Lurking in Your Inbox?
What Phishing Threats Are Lurking in Your Inbox? It’s well known that a good security strategy calls for layers of protection to thwart bad actors from quickly accessing sensitive data. While many organizations have a secure email gateway deployed to catch threats with malicious links and attachments, many criminals have discovered that they can use various strategies to get through those systems and land in the victim’s inbox. Below are some threats that could be lurking in your inbox
Read Blog
How Much Does Phishing Cost Businesses?
How Much Does Phishing Cost Businesses? Cybercriminals have relied on phishing emails as a gateway to gaining access to sensitive information since the beginning of email. And reports indicate that this isn’t slowing down. For threat actors, phishing is a lucrative business made profitable through various activities like a direct ransomware attack. The success and profitability of phishing have led threat actors to offer Phishing-as-a-Service offerings that bypass SEGs for $1,500.
Read Blog
What Is Your Company’s REAL Click Rate On Phishing Emails?
What Is Your Company’s REAL Click Rate On Phishing Emails? Sometimes I hear the following from security professionals when we talk about their awareness program: "We are averaging a 2-3% click rate on our phishing simulation program; we are in a great place!” My immediate answer is: “How difficult are your phishing templates?”
Read Blog
Is Your Organization Vulnerable to Account Takeover?
Is Your Organization Vulnerable to Account Takeover? Almost every business or organization is a target for account takeover (ATO) attempts. There’s a good chance that your organization is vulnerable. What is an account takeover attack? Simply defined, it’s when a cybercriminal gains access and control of another party’s legitimate account (such as a Microsoft O365 or Google Workspace account). An ATO attack is more than just a data breach. An ATO attacker gains full control to make purchases, transfer money, steal bank and credit card information, gain access to sensitive business intelligence, or even disrupt business operations—all before a user even knows the account has been compromised.
Read Blog
3 Ways Your SEG is Failing Your Email Security Strategy
3 Ways Your SEG is Failing Your Email Security Strategy Secure Email Gateways (SEG)s have been a staple in many organizations’ strategies to curb email phishing and spam messages from disrupting business and targeting employees. They’ve become so commonplace that many email clients include their own version of the technology as a free tool. Unfortunately, SEGs have yet to adapt as rapidly as the strategies threat actors use to bypass them-which is a reason why phishing emails continue to be the entry point for data breaches.
Read Blog
Will Deepfake Emails Lead to Phishing 3.0?
Will Deepfake Emails Lead to Phishing 3.0? For good and bad, AI is now more accessible and used for things from writing articles to identifying phishing threats. For anti-phishing, AI accessibility is beneficial for building better cyber security solutions, automating the investigation and response processes, and increasing prevention and detection—resulting in the ability to identify and mitigate massive volumes of phishing threats quickly.
Read Blog
New Study Finds Phishing Represents a Huge Time and Expense Burden for Organizations
The Business Cost of Phishing report reveals organizations with 25 IT and security professionals are spending more than $1 million per year to handle phishing
Read Blog
Nag Attacks: The Latest Evolution of Phishing
It may be wrong to admit, but I love a good con. It is the art of deception that fascinates me the most. Watching a con artist at work is enthralling and fills me with a mix of surprise at their audacity and elation that it didn’t happen to me. To gain the mark’s confidence, the con artist systematically exploits their psychology. In the world of cyber-security, we simply refer to the con artist as a cybercriminal, much less of a romantic term. While the art of a deceptive phishing email is constantly evolving, the principles remain the same—to gain the confidence of the mark (phishing recipient) for financial gain.
Read Blog
What aviation can teach you about email security
What aviation can teach you about email security Defense in depth is a common practice in both the physical and the cyber security realms. We create multiple layers to complement each other; each layer assumes its predecessor failed. I travel a lot, and I find aviation security fascinating. It is a well-thought, well-orchestrated security process designed to detect and prevent various threats, most of which are based on known events. When you look at how aviation handles security and compare it to email security, you can see similarities as well as opportunities to build stronger parameters.
Read Blog
Leveraging AI and Human Intelligence in Email Security
The Artificial Intelligence (AI) vs. Human Intelligence (HI) debate has been discussed a lot in the past few years. There is no doubt that AI can outperform humans in specific areas and even beat the human world champion in chess. However, AI algorithms still have a very long way to go to match the human brain’s capacity. And despite the fact AI systems were modeled and trained to mimic human behavior, they, too, make logical judgments like we can. The ability of AI to make decisions is mostly based on inputs, i.e., the data they’re trained on, so no matter how good your models are, they are only as good as your data!
Read Blog
Ransomware Gangs: Lapsus$
The 2022 Uber Breach: Social Engineering and the Lapsus$ Gang A cyber-attack on ride-hailing company Uber made global media headlines in September 2022 when a threat actor infiltrated the company’s internal systems. Social engineering techniques featured prominently in the incident, which was purportedly carried out by a threat actor affiliated with the Lapsus$ extortion gang. This article overviews Lapsus$ and analyzes the important cybersecurity details from the Uber breach.
Read Blog
The 1%
It seems like there are two or three posts every day on social media where cyber security companies are basically saying, “Don’t trust humans to keep your company secure because they’ll always fail. Instead, trust our [insert whizbang product name] that uses the latest in AI/ML to keep your company safe.” We are proud of what our AI/ML can do when it comes to detecting and remediating advanced phishing attacks - and doing so in just milliseconds. We can show that our AI/ML is stopping around 99% of advanced phishing attacks, but we acknowledge that some of our fellow ICES-type email security companies are probably catching about the same amount with their AI/ML. The question then becomes: what happens with the other 1%? That’s where we have taken a different path than the competition.
Read Blog

How to Improve Your Email Security in 24 Hours
How to Improve Your Email Security in 24 Hours Cybersecurity Awareness month is right around the corner. As such, you may be assessing your business’s risk profile to identify weaknesses and targets. With phishing attacks being a leading cause of data breaches and ransomware attacks, security and IT leaders take this time to address email security vulnerabilities. This post covers three tips and resources you can use to quickly strengthen your email security posture and defense against phishing attacks.
Read Blog
The Case Against URL Rewriting For Email Security
The Case Against URL Rewriting For Email Security URL Rewriting, a service used to sandbox and defang malicious URLs by sending users to a portal that displays the URL in the sandboxed environment, has many well-known weaknesses and a few that may not be obvious. This article aims to identify these weaknesses and offer our thoughts on a different strategic approach for email security. We will cover how URL Rewriting services can undermine a defense-in-depth strategy, limit security culture development, fail technically, and give a false sense of security when dealing with Business Email Compromise (BEC) attacks.
Read Blog
5 Email Security and Phishing Predictions for 2022 (Part 2)
5 Email Security and Phishing Predictions for 2022 (Part 2) Being prepared for the latest email security and phishing threats requires anticipating what’s on the horizon over the next year or so. Part one of this series of predictions covered the possible emergence of deep phishing, the evolution of ransomware gangs, and more. Here is what else 2022 may have in store from an email security and phishing perspective.
Read Blog
5 Email Security and Phishing Predictions for 2022 (Part 1)
5 Email Security and Phishing Predictions for 2022 (Part 1) In the dynamic world of cybersecurity, things change quickly and often—email security and phishing are no exceptions. Each 12-month period sees a range of new tactics, tools, and methods employed by threat actors trying to break into networks through phishing messages. This article runs through some of the top predictions for email security and phishing as 2022 unfolds.
Read Blog
Ransomware Gangs: 0ktapus
Ransomware Gangs: 0ktapus In 2022, a large-scale phishing campaign successfully compromised IT resources at over 130 organizations, many of which were high-profile companies. Code-named 0ktapus, the threat group behind this attack used relatively primitive hacking methods and smart planning to achieve its aims. This article analyzes the operations of 0ktapus’ threat actors and overviews some critical lessons learned about the commonplace security measures that modern businesses deploy to protect their information systems and data.
Read Blog
Vendor Spoof Attack Exposes Business Email Credentials
Vendor Spoof Attack Exposes Business Email Credentials A researcher at IRONSCALES recently discovered thousands of business email credentials stored on multiple web servers used by attackers to host spoofed Microsoft Office 365 login pages. The researcher found the credentials while investigating a new string of Vendor Impersonation phishing emails designed to execute Account Takeovers (ATO) and Business Email Compromise (BEC) attacks.
Read Blog
The State of Ransomware Attacks in the Retail Industry
The State of Ransomware Attacks in the Retail Industry Ransomware attacks pose serious cybersecurity risks for retailers. If an attack manages to disrupt customer-facing operations during peak business periods, it could have a disastrous effect on a retailer’s bottom line. This article looks at the state of ransomware in the retail industry by focusing on recent attacks and the lessons retailers can learn from them.
Read Blog
How Account Takeover (ATO) Attacks Work
How Account Takeover (ATO) Attacks Work Account takeover (ATO) attacks involve threat actors gaining access to and control over legitimate user accounts. After taking control of a user’s account, the malicious actor then uses the account’s credentials to launch further attacks. One recent study found that ATO increased by 90 percent from 2020 to 2021. Cybercriminals increasingly target individual personal and business accounts as initial attack vectors because it’s efficient and doesn’t depend on sophisticated techniques.
Read Blog
Ransomware Gangs: Evil Corp
Ransomware Gangs: Evil Corp Evil Corp is a cybercrime gang notorious for its prolific malware-based hacking schemes leading to payments exceeding $100 million from various financial institutions and other businesses. The ransomware gang’s level of notoriety is such that the U.S. government issued sanctions against it, charged two members with criminal violations, and announced a $5 million reward for information leading to its leader’s capture or conviction. The shape-shifting nature of Evil Corp in recent years has seen the gang’s members and affiliated operations deploy a number of different ransomware strains and tactics making it difficult to attribute their involvement in the cyber attacks. This article analyzes Evil Corp’s operations and ransomware deployments to help identify patterns and avoid attacks.
Read Blog
The Three Must-Haves of a Truly Automated Email Security Solution
The Three Must-Haves of a Truly Automated Email Security Solution Today, everything is automated. Our daily routines, our responses to simple questions such as “how was your day,” the train you take to get to work, the sell price for stocks – all automated. But even with those examples provided, how many of those functions are truly automated to where no human interaction or intervention is required?
Read Blog
To Prevent Email Phishing Risks, It’s a Race Against the Clock
To Prevent Email Phishing Risks, It’s a Race Against the Clock When it comes to beating a phishing attack, organizations are not only trying to beat the malicious message itself; they are also trying to beat time. That’s because the median time to click on phishing attacks is less than two minutes. That’s a very short window of time for something so simple as an email to cause catastrophic harm to your organization.
Read Blog
3 Ways to Boost Awareness and Prevent Phishing Attacks
3 Ways to Boost Awareness and Prevent Phishing Attacks When it comes to email security, no amount of technology can completely stop the threat of phishing attacks. As the threat landscape evolves and cybercriminals identify new methods to breakthrough secure email gateways or AI-only anti-phishing solutions, your employees become the last line of defense to protect your data and your reputation. To empower them to make informed, confident decisions and minimize the chance of an attack, you’ll want to ensure that your employees' security knowledge is up to date and top of mind. This post provides three quick tips to help boost your employee’s cybersecurity awareness and avoid phishing threats.
Read Blog
Is It Finally the Time To Let AI Drive Our Cyber Defenses and Security Operations?
Is It Finally the Time To Let AI Drive Our Cyber Defenses and Security Operations? Cyber security is a tough challenge, and it's getting harder to keep up with the latest threats. AI-powered tools leveraging machine learning can help detect phishing attacks by analyzing huge amounts of data in seconds rather than hours. These new email security solutions have proven to be up to 10 times as fast and significantly more accurate than legacy signature-based systems, as the older systems require constant updates from vendors due to changes within their code base. The new AI/ML-driven solutions also solve the problem of downtime for maintenance, as those changes are handled from within the platform automatically with zero impact on the tool’s performance or end-user experience.
Read Blog
The Cons of Email Blocklists
The Cons of Email Blocklists For organizations dealing with phishing attacks, it may seem like an easy solution to stopping the attacks is just to block the attacker. Turns out that isn’t the case. Let’s look at why this approach actually creates more work for your already overburdened security team.
Read Blog
The Evolution of Email Security from Spam Filters to Business Email Compromise Protection
The Evolution of Email Security from Spam Filters to Business Email Compromise Protection Ever since email went mainstream, hackers and spammers have been bombarding inboxes with unwanted messages, phony ads, fraudulent links and viruses. And every time internet service providers (ISPs) and security vendors devise tools and techniques to eliminate or reduce the threats, fraudsters have found new ways to get around the newly created defenses. This has remained true since the time of spam mitigation in the early 2000s to the business email compromise (BEC) protection challenges of today.
Read Blog
Sorry To Burst Your Optimism
Sorry To Burst Your Optimism Every family has its IT guy, ours is Raphael and he is great at it. Embracing this position within the family he married into, Raph faithfully keeps us updated on WhatsApp with interesting articles and important security updates. About a year and a half year ago he sent one of those updates and included a phishing quiz. With the confidence that is becoming of a Product Manager in the Israeli high-tech scene, I embraced the challenge and… failed miserably. Ironically enough, I got a call eight months later from David Habusha, vice president of product management at IRONSCALES (an industry leader in email security) about an opportunity to join the team. The memory of failing Raphael’s phishing quiz was still fresh in my mind.
Read Blog
We Adds Security Awareness Training
IRONSCALES Adds Security Awareness Training Many people don’t know that IRONSCALES started as a Security Awareness Training company. While working as a security researcher at a technology company, Eyal Benishti (our founder & CEO) had a steady stream of coworkers asking him every day about whether an email they’d received was a phish or if it was safe. Eyal decided to write a piece of software that could help train end users like his coworkers on the basics of spotting phishing attacks. Building on this, he developed new functionality that could detect and remediate phishing attacks. Fast forward nearly a decade and that’s exactly what IRONSCALES is still doing for our customers today–fighting back against phish and training end users with a single, integrated solution.
Read Blog
How your university can reduce the threat of cyberattacks
How your university can reduce the threat of cyberattacks Eyal Benishti, CEO and Founder, IRONSCALES August 3, 2022 Cyberattacks aren’t a challenge to take lightly--all it takes is one click to impact an entire campus We’ve seen an alarming rise in the number of cyberattacks against universities in the last few years, particularly as schools moved entirely or partially online during the COVID-19 pandemic. CSO reports that cyberattacks on education and research targets increased an astonishing 75 percent between 2020 and 2021. These attacks threaten to take critical functions offline, disrupting teaching and research, and put sensitive data at risk. And with many universities coping with already reduced budgets, paying to recover lost data can make a crunch worse.
Read Blog
Ransomware Gangs: Cuba
Ransomware Gangs: Cuba While several high-profile ransomware gangs saw a steep rise and an equally sharp decline over the last couple of years, Cuba ransomware somewhat slipped under the radar. With the gang behind Cuba ransomware amassing over $40 million during a spate of attacks on critical infrastructure in 2021, it’s important to learn about Cuba’s origins, operations, and victims.
Read Blog
Ransomware Gangs: Egregor
Ransomware Gangs: Egregor Egregor is a ransomware-as-a-service gang that has so far managed to claim at least 70 victims and extort tens of millions of dollars during a prolific yet short spell of operations. The Egregor ransomware strain first surfaced in September 2020, and most attacks occurred within a three-month period, ending in December 2020.
Read Blog
A SEG By Any Other Name Is Still A SEG
A SEG By Any Other Name Is Still A SEG The email security market is full of vendors offering a wide array of features and capabilities. To make sense of the chaos and to bring clarity to companies seeking the right solution for their specific email security challenge, Gartner broke the market into three segments and aligned vendors to each: Secure Email Gateways (SEGs), Integrated Cloud Email Security solutions, and Email Data Protection solutions. Here is a summary of each segment as stated in the most recent Gartner Market Guide for Email Security:
Read Blog
Crypto Phishing Scam
Crypto Phishing Scam Cryptocurrency is a digital medium of exchange that is not associated with traditional currency-issuing institutions like national banks. Instead, cryptocurrency is managed using blockchain technology that runs on distributed computers and networks across the internet. The cryptocurrency market has exploded in recent years, both in the number of cryptocurrencies available for use as well as investors placing bets on which one(s) will grow in value.
Read Blog
Resource efficiency vs. maximum security – why they don’t have to be at odds
Resource efficiency vs. maximum security – why they don’t have to be at odds At its core, your email security team has one simple goal: protect company emails from compromise. The solution they choose to meet that end often involves a patchwork of monitoring, data collection, analysis, and mitigation tools. It’s not always the most efficient approach and, as threats get more advanced, it doesn’t always keep pace.
Read Blog
The State of Ransomware Attacks in the Manufacturing Industry
Disrupting operations at manufacturing plants is a potentially lucrative path for threat actors specializing in ransomware. This article discusses the current state of ransomware in the manufacturing sector by focusing on the vulnerabilities, statistics, and some recent attacks.
Read Blog
Ransomware Gangs: Black Basta
Ransomware Gangs: Black Basta After a cull that saw several high-profile ransomware gangs disbanded in late 2021 a new set of groups emerged in their place. One gang with a particularly rapid rise over the last few months in Black Basta. This article analyzes the origin of Black Basta, its ransomware operations, and its victims.
Read Blog
Ransomware Gangs: Netwalker
Ransomware Gangs: Netwalker Netwalker is a notorious name on the ransomware scene with a prolific record of successful attacks. An estimated $25 million in ransom extortions between March and September 2020 established the gang as a force to be reckoned with. This article looks at Netwalker's operations, the specifics of the ransomware variant, and some high-profile attacks carried out using Netwalker ransomware.
Read Blog
Smishing Attacks Explained
What Is Smishing? Smishing is a type of social engineering scam that uses mobile texting rather than emails to deliver nefarious messages that dupe people into taking specific actions. The term is a combination of phishing and SMS, and its increasingly widespread use reflects a belief among cybercriminals that people are generally more likely to trust the contents of text messages over emails. Threat actors often text people directly using traditional SMS, but smishing also encompasses messages sent via apps like WhatsApp, Viber, or other messaging apps that require users’ phone numbers. Industry reports and studies continue to highlight the growing prevalence of smishing attacks. One survey reported by Statista found that 74% of organizations and IT professionals experienced smishing attacks during 2021. This figure represented a 13% increase from the previous year.
Read Blog
Wave of Phishing Attacks Possible with OpenSea Data Breach
Wave of Phishing Attacks Possible with OpenSea Data Breach OpenSea, the largest non-fungible token (NFT) marketplace, disclosed a breach on their blog on June 29, stating that an employee of Customer.io, their email delivery vendor “misused their employee access to download and share email addresses – provided by OpenSea users and subscribers to our newsletter.” They went on to advise users to be alert for phishing emails that may attempt to impersonate OpenSea via email. Attackers have been targeting OpenSea users with phishing messages for some time, but this breach will certainly lead to a wave of phishing emails targeted at the estimated 600k leaked email addresses that are probably already being sold on black markets. Since these email addresses will likely be listed as known NFT wallet holders, other NFT platform brands will probably be impersonated with “offer, trade, transfer” themed phishing email attacks.
Read Blog
Ransomware Gangs: FIN7
FIN7 is a unique group in the shady world of cybercrime. Infamous for sophisticated stolen credit and debit card hacks involving phishing emails and other social engineering methods, the gang’s threat actors deploy a range of constantly evolving tactics to steal money; the latest of those tactics is ransomware. This article overviews FIN7’s operations.
Read Blog
Whaling Attacks Explained
What is Whaling? Whaling is a type of spear phishing in which threat actors directly target c-level executives at an organization. This type of social engineering attack sends fraudulent messages to individuals with high levels of seniority to exploit three particular characteristics of these C-suite roles: High levels of information knowledge about the organization High levels of access to different systems, accounts, and sensitive data High levels of authority to perform secondary actions, such as transferring funds, without requiring approval
Read Blog
Avoid Being Scammed When Buying FIFA World Cup 2022 Tickets
The World Cup Ticketing Scam If you're one of the estimated 3 million football/soccer fans looking to buy tickets to this year’s FIFA World Cup, beware of fake emails like the one below. There have been reports of people receiving email messages claiming to be from FIFA, the organization responsible for the World Cup, offering tickets for sale. In reality, these messages are phishing attempts.
Read Blog
Business Email Compromise (BEC) Explained
What is Business Email Compromise? Business email compromise (BEC) is a type of targeted phishing (spear phishing) in which a threat actor either accesses or mimics a genuine business email account to defraud the business. This tactic relies on exploiting the assumed trust that victims have in emails coming from what appear to be genuine sources. Often, these scams target employees working in financial departments or executives who have the power to transfer money from business accounts to bank accounts under the control of the threat actor. BEC is a notably high-cost type of phishing attack. In fact, the FBI released a Public Service Announcement in 2022 outlining that BEC cost companies an estimated $43 billion between 2016 and 2021.
Read Blog
Detecting and Remediating EMOTET Malware
EMOTET malware is a banking trojan that was initially spotted in 2014, disappeared for a while, and then reappeared in 2018. EMOTET is typically spread through phishing emails with malicious Microsoft Word or Excel files attached. Should an end-user click on the malicious attachment, the malware will begin running on their machine. This, in turn, allows the threat actor to deploy specific types of malware to the victim’s machine which could range from banking trojans, ransomware, keyloggers, and more.
Read Blog
The State of Ransomware Attacks in the Transportation Industry
Transportation companies provide critical functions in shipping products and carrying people to their destinations. Encompassing both transport and logistics companies, the transportation sector is at a high risk of exposure to ransomware attacks that can disrupt services or even endanger peoples’ welfare. This article examines the current state of ransomware in transportation.
Read Blog
Developing a Healthy Distrust for Email in the Workplace
A half-century has passed since the first electronic messages were sent via connected ARPANET computers. It was roughly a decade later than we began calling these transmissions “email.” In the decades since, email has become such a ubiquitous part of everyday life – shaping how we communicate, do business, shop, market products, pay bills, find jobs, and so much more – that we tend to overlook how vulnerable it leaves us.
Read Blog
What Is Ransomware: Demystifying and Defending Against an Evolving Threat
“I know I hear you talk about this all the time, but what is ransomware exactly?” my wife asked as we watched the evening news. Apart from being a great question, it’s one that a lot of folks have been pondering lately. And so, in this this blog we will demystify and define the phenomenon. We will discuss its history, how the term grew to be so common, and offer some ideas of what the future might hold as ransomware evolves.
Read Blog
The Human Factor in Email Phishing
“Yeah, I get it, but I just don't trust users; they always screw everything up,” lamented the Director of IT, while on a recent sales call featuring our dynamic contextual awareness banners. His is not a unique viewpoint. Distrust in the capabilities of non-technical employees is a common perspective among technologists and one that I admit to once sharing. However, after spending most of my life in information technology and cybersecurity, I now realize employees are a critical, necessary element of every company’s security response, especially when it comes to email phishing.
Read Blog
New Dog, Old Tricks: Reducing Cryptocurrency Phishing Vulnerabilities
For the security-minded, the rise of cryptocurrencies has been both a blessing and a curse. Coins like Bitcoin and Ethereum theoretically offer a higher degree of protection and privacy than traditional banking, especially in an online world where banking websites share much of our sensitive financial information with untold numbers of third-party vendors. Having full control of a cryptocurrency wallet, with strings of numbers serving as the username and password rather than any personally identifiable information
Read Blog
Is a lack of quality talent stretching your security team too thin?
If you’re concerned that your security team may be suffering from fatigue, lacking motivation, or feeling overwhelmed… you’re not wrong. The industry is facing a dearth of qualified cybersecurity professionals, and that skills shortage is causing problems for organizations large and small, as the barrage of cyber threats grows ever more constant.
Read Blog
The State of Ransomware Attacks in the Healthcare Industry
The sensitive nature of information gathered about patients makes healthcare organizations particularly vulnerable to ransomware attacks. Seeking a large payday, opportunistic hacking groups target the healthcare sector believing that disrupting critical patient services or stealing valuable data is more likely to result in payouts. This article looks at ransomware in healthcare by focusing on some recent incidents, statistics, and mitigation strategies.
Read Blog
Four Benefits of Automated Advanced Phishing Threat Protection to the Channel
Fostering channel partnerships with reputable value-added resellers (VARs) has become an important component of most cybersecurity companies go-to-market strategies. Challenged by what seems like historic levels of market saturation and the continued emergence of new and potentially disruptive technologies, many InfoSec product and service providers have come to depend on the channel not just to expedite sales and sustain revenue, but also to aggressively protect against competitors seeking to make a dent in their mindshare and market share.
Read Blog
The State of Ransomware Attacks in the Manufacturing Industry
Disrupting operations at manufacturing plants is a potentially lucrative path for threat actors specializing in ransomware. This article discusses the current state of ransomware in the manufacturing sector by focusing on the vulnerabilities, statistics, and some recent attacks.
Read Blog
Ransomware Gangs: FIN7
FIN7 is a unique group in the shady world of cybercrime. Infamous for sophisticated stolen credit and debit card hacks involving phishing emails and other social engineering methods, the gang’s ...
Read Blog
Ransomware Gangs: BlackCat
International law enforcement collaboration led to the disbandment of several high-profile ransomware gangs in the last 12 months. As ransomware attacks gained more media coverage and wreaked more ...
Read Blog
Ransomware Gangs: Netwalker
Netwalker is a notorious name on the ransomware scene with a prolific record of successful attacks. An estimated $25 million in ransom extortions between March and September 2020 established the gang as a force to be reckoned with.
Read BlogWhy “Search and Delete” Won’t Get The Job Done
Here at IRONSCALES, we often speak with organizations about their messaging incident response process. And we’ve learned that all too frequently, the primary response tools are 1) an email search and then 2) a deletion operation on the messages identified from that search. We call this a “search-and-delete” incident response strategy.
Read BlogRansomware Gangs: Babuk
Babuk is a new ransomware gang that emerged in early 2021. The gang’s initial mission statement referenced a non-malicious intent to conduct ransomware attacks as an apparent audit of the security of corporate networks. The reality of Babuk’s operations, however, does not align with this non-malicious intent, as the gang has exfiltrated sensitive data from organizations in law enforcement and others. This article analyzes Babuk’s operations, ransomware strain, and victims.
Read Blog
Ransomware Attack that Employed Reverse Psychology to Trick Victims
Ransomware attacks have been on the rise throughout 2021, affecting everyone from large enterprises and government organizations to the individual end-user. Many such attacks are executed via a phishing email, taking advantage of an accessible and exploitable endpoint. This attack demonstrates the criminals’ savvy use of social engineering to lay the first step of the trap.
Read Blog
FBI Domain Spam Campaign
Hackers can use their abilities to do good, to do bad and sometimes just to show what they can do. The last option was the case for this scenario.
Read Blog