
Detecting and Remediating EMOTET Malware
EMOTET malware is a banking trojan that was initially spotted in 2014, disappeared for a while, and then reappeared in 2018. EMOTET is typically spread through phishing emails with malicious Microsoft Word or Excel files attached. Should an end-user click on the malicious attachment, the malware will begin running on their machine. This, in turn, allows the threat actor to deploy specific types of malware to the victim’s machine which could range from banking trojans, ransomware, keyloggers, and more.
So how does IRONSCALES protect customers from EMOTET attacks? Before answering that question, it is important to note that EMOTET is malware that has already been delivered into an end-user’s mailbox and has been unwittingly activated by the victim. The IRONSCALES solution is designed to detect and remediate threats like this before an end-user ever has the chance to see the email, let alone to click on the malicious Microsoft Word or Excel attachment.
Here is how the IRONSCALES solution would protect against this specific attack:
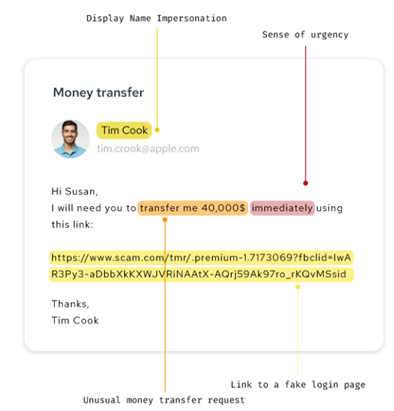
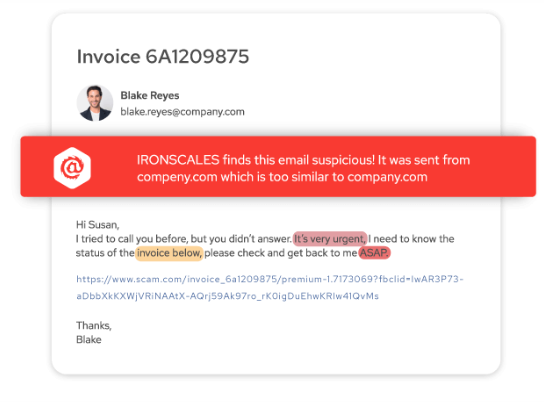
- At the time of implementation, we do a 90 day scan back of every protected mailbox so that we can learn what “normal” email communications for each employee looks like. Using this social graph information, our AI-based behavioral models will flag any unexpected emails being received. For example, if an employee in marketing typically only communicates with other members of the marketing team and then one day, she gets an email from the CFO instructing her to order one hundred Amazon gift cards, our platform will flag that email as suspicious based not on the content of the email, but the intent of the email. Using our Natural Language Processing capabilities, our platform will also recognize that the language (“Go buy the Amazon gift cards quickly!”) in the email matches that of other known phishing emails. Our solution can be configured to automatically pull identical or similar emails out of all the company’s inboxes automatically, quarantine the email and wait for the company’s IRONSCALES administrator to decide or place a warning banner in the email to let the recipient know that we believe there’s a potential risk with the email and to proceed with caution.
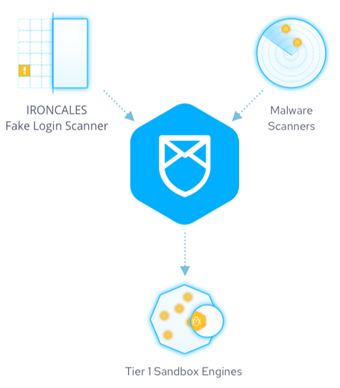
- In addition to our Natural Language Processing and AI-driven detection and remediation, our platform also leverages over seventy (70) third-party scanners to review every attachment that comes into the customer’s email environment and determine if the attachment is malicious or not based on known signatures. we send every attachment to our third-party sandbox to review and determine if the attachment is malicious or not. Finally, and unlike traditional Anti-Virus (AV) tools, the IRONSCALES platform does not just do a single scan on an attachment; rather, we continue to scan attachments for several days to look for time-detonated malicious attachments and links that may have bypassed the AV engines initially.
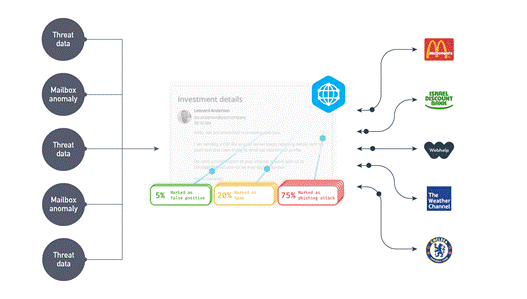
- In addition to our AI/ML, Natural Language Processing, and 70+ third-party scanning engines reviewing every email, attachment, and link that comes into a customer’s environment, IRONSCALES also offers something that no other provider provides: crowdsourced threat intelligence. We call this the “IRONSCALES Community”, which every one of our 7,000+ customers joined on their first day with us. The Community allows our customers’ security teams to anonymously report new email-based threats to us via their customer portal, which allows us to then extend protection against this new threat to all our customers automatically. Community members can even communicate anonymously with one another about specific threats through their customer portal as well.
In summary, the IRONSCALES solution is built to stop EMOTET attacks using a multi-layered, fully integrated set of capabilities. First, we analyze every single email and attachment that is sent to our customers. We review the language of the email for suspicious intent using Natural Language Processing and known behavioral baselines for each end-user. We review the attachments using over 70 third-party scanning tools as well as sending every attachment to a third-party sandboxing tool for evaluation. And finally, we incorporate crowdsourced threat intelligence from the security teams at our 7,000+ customers to identify new threats before they can impact our customer base.