Blogs
Explore SRC Cyber Solutions LLP Blogs
Discover how our solutions have empowered organizations to overcome challenges, achieve operational excellence, and drive transformative growth. Learn from real-world success stories.

SRC Cyber Solutions: Delivering Value & Safeguarding Enterprises through Innovative & Reliable Smart Threat Intelligence Solutions
A technology distributor that enables individuals and enterprises to safeguard their data by providing a comprehensive suite of...
Read Blog
MSPs and SIs: Deliver Enterprise-Grade Cybersecurity for Any Customer, Even Just Five Users
Cyber threats are evolving, and employee awareness is key to defense. SRC Cyber Solutions offers expert-led security training, phishing simulations, and GRC solutions to build a cyber-resilient workforce.
Read Blog
The Hidden Gaps in Email Security What Your SEG Isn’t Catching
The Hidden Gaps in Email Security: What Your SEG Isn’t Catching
Read Blog
Security Awareness and Training: Strengthening Cyber Resilience with SRC Cyber Solutions
Security Awareness and Training: Strengthening Cyber Resilience with SRC Cyber Solutions
Read Blog
Keeping Business Data Safe: How SRC Protects Companies Worldwide
SRC Cyber Solutions LLP (SRC) believes that every business deserves strong protection from digital cyber threats without needing a dedicated team of technical experts.
Read Blog
SRC Cyber Solutions Ushering in Next Generation Technologies to Combat Cybersecurity Threats
The digital age, along with its many benefits also has a flipside Cybersecurity threats. With the passage of time, hackers with their malicious intent to cause cyberattacks which have grown at a pace that is hard to combat. Protecting critical information and infrastructure from cyberattacks, has be
Read Blog
SRC Cyber Solutions Revolutionizing Cybersecurity with Astute Solutions
Technological innovations have revolutionized the way we use Software Applications, Computer Hardware, Cloud Computing, and the Internet today. With the increasing dependency, the number of cyber threats has also increased exponentially. The demand for high-quality cybersecurity solutions, thus, has
Read Blog
Anticipating the Future: Three Enterprise Email Security Predictions to Bolster Your Team's Defenses
With 2023 now officially behind us, I think it’s safe to say that 2023 will be etched into the timeline of tech history as the year AI entered the mainstream. And what an entrance it made. Before the first month of 2023 had come to a close, ChatGPT had already become the fastest-growing consumer app
Read Blog
Alert: Indian Investors Beware of Chinese Cybercriminals' Phishing via Fake Brokerage Apps
The harsh truth of losing life savings to deceitful apps mimicking reputable Indian brokerages is deeply impacting investors causing a rise in Phishing scams. Remain vigilant to steer clear of these intricate schemes from Malware, Phishing, Fake Login Pages, Phsihing Websites and fake URLs. Add
Read Blog
European Union Dora
In the evolving landscape of digital operations within the FinancialSector, the enactment of the Digital Operational Resilience Act (DORA) by the European Union underscores the imperative for robust CyberSecurity measures.
Read Blog
Address data breaches with proactive data Risk Management Solutions
Recent #DataBreach underscores the urgent need for robust #DataManagement strategies. With breaches becoming recurring, establishing control over #DataFlow is important. Our #ThirdPartyDataFlow solution offers an effortless golden catalog, mapping data flows and implementing #RecoveryPolicies. With
Read Blog
76% Manufacturers face Phishing Threats in their digitally transformed landscape
Manufacturers face a rising tide of #PhishingThreats in their digitally transformed landscape. With 76% adopting digital tools, vulnerabilities, especially Vendor Email Compromise, are on the rise.
Read Blog
Safeguard your Inbox Protect against AI in Phishing Attacks
#GenAI revolutionizes #Phishing, enabling attackers to craft sophisticated #SocialEngineering content in seconds. The traditional trade-off between quality and quantity is done as #Malicious actors harness #AI diversity to scale operations across various formats, styles, and languages.
Read Blog
Don't Get Hooked Recognizing Phishing Red Flags for a Safer Online Experience
The red flags for #PhishingAttacks, emphasize vigilance against scare tactics, and #UnsolicitedValls. Lookalike #WebAddresses, and #SuspiciousAttachments.
Read Blog
Rs. 52 Crore Fraud from Cybersecurity Breach
A detrimental Rs. 52 crore fraud, spotlighted by reputable media sources, unfolded due to a #EmailSecrutiy lapse, exposing compromised business IDs and enabling unauthorized transfers. The main reason for this breach was poor #EmailSecuritySolutions.
Read Blog
How can a phishing attack impact you ?
Guard your digital wall! A #PhishingAttack can devastate your personal and #Financial security. Clicking on #MaliciousLinks or sharing #SensitiveInformation puts you at risk of #IdentityTheft, #FinancialLoss, and #CompromisedAccounts. Stay vigilant, protect your online presence, and learn the signs
Read Blog
Many Festivals One Name
Wishing our Customers, Partners, and Friends a joyous #MakarSankranti, #Lohri, #Pongal, and #Bihu!
Read Blog
Phishing has led to incidents like Sextortion and Job Scams, resulting in 129 cases per 1 Lakh individuals in India
In 2023, India faced a surge in #Cybercrime with 129 reported incidents per 1 lakh citizens. Delhi topped the list with 755 complaints, followed by Chandigarh and Haryana.
Read Blog

Cyber heists cost India a staggering 10,000+ Crores over 3 years
No description available.
Read Blog
Scam-as-a-Service facilitating cybercriminals in cryptocurrency wallet-draining attacks
No description available.
Read Blog


Importance of Security Awareness Training (SAT) in Cybersecurity Landscape
In today’s digital era, where cyber threats loom large, the significance of security and awareness training cannot be overlooked.
Read Blog

5 Key Benefits of Automated Patching for Modern Endpoint Security
Automated patching has become an integral part of modern-day endpoint security strategies, offering many benefits that enhance the overall cybersecurity landscape. In today’s rapidly evolving threat environment, where cyber-attacks are evolving and becoming more sophisticated, maintaining a robust d
Read Blog
What is E-mail security? A comprehensive guide
Email has transformed the way we communicate, but with its convenience comes a multitude of security risks.
Read Blog
The Future of Cyber Security: Trends to Watch Out
In an era defined by rapid technological advancement, the landscape of cybersecurity is evolving at an unprecedented pace.
Read Blog
How AI Can Help You Protect Your IT Environment from Cyber Threats
In a time where digitization has increased, the importance of safeguarding your IT environment from cyber threats cannot be ignored. As technology advances every day, so do the tactics of cybercriminals, which makes it important for enterprises to stay one step ahead. Enter Artificial Intelligence (
Read Blog
SRC Celebrating the 2023 Cyber Security Awards
In the fast-growing digital age of 2023, where technology affects every aspect of our lives, ensuring the security of our personal information has become paramount. This rise of technology has brought many benefits, but it has also exposed many new threats and vulnerabilities. Fortunately, there are
Read Blog




Validate the ongoing Threats to your Switches and Ports to ensure Cyber Resilence
Validate the ongoing Threats to your Switches and Ports to ensure Cyber Resilence
Read Blog


Wishing our Friends, Partners and Customers a #HappyHoli !
#Holi is a popular ancient Hindu festival, also known as the Festival of Love, the Festival of Colours, or the Festival of Spring. Holi celebrates the arrival of spring, the end of winter, the blossoming of love and for many, it is a festive day to meet others, play and laugh!
Read Blog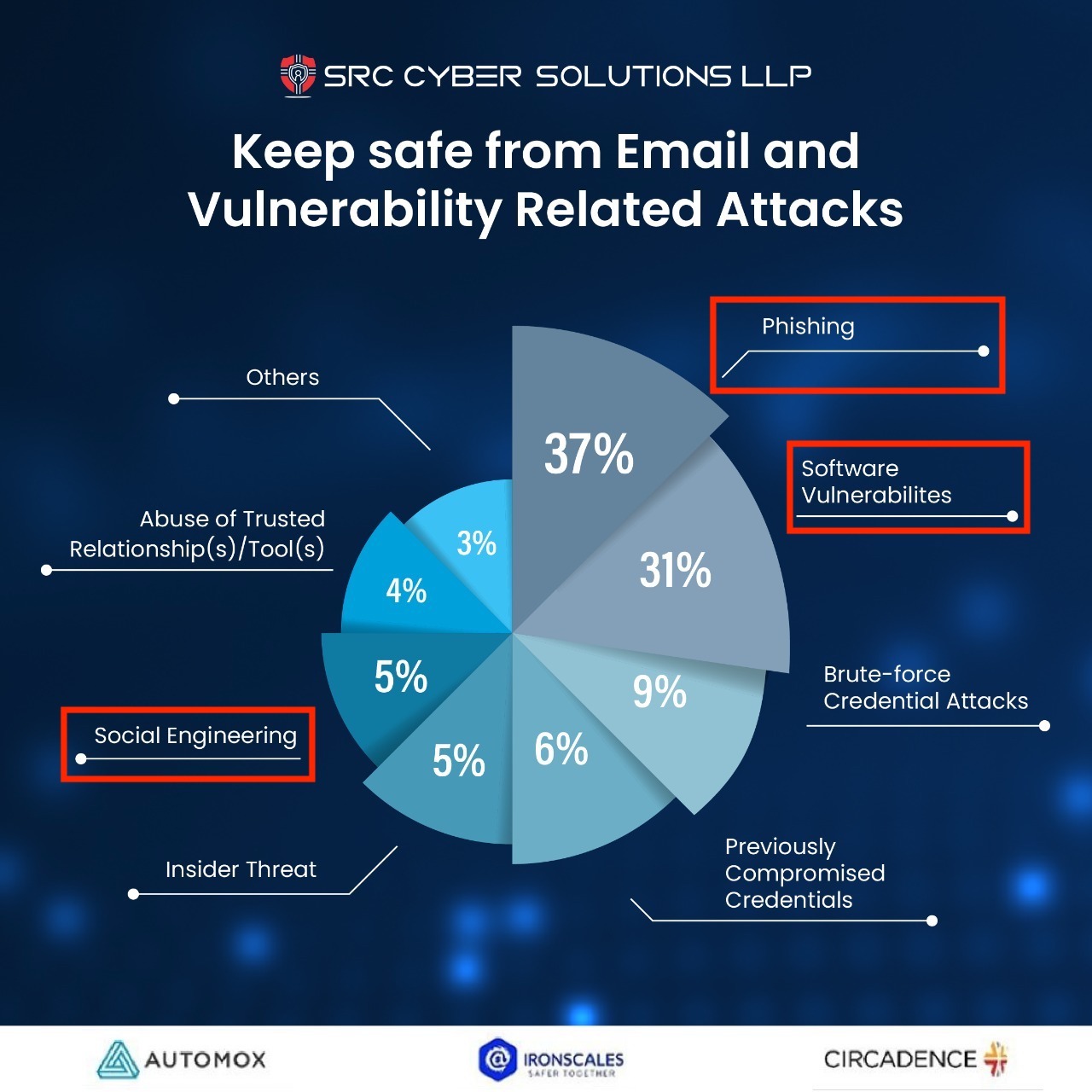
A recent report tabulated the most "Suspected Means of Initial Access" into an Organisation! #Phishing #SocialEngineering and #Vulnerabilities are the most used form of access, accounting for a shocking 72% of the cases.
A recent report tabulated the most "Suspected Means of Initial Access" into an Organisation! #Phishing #SocialEngineering and #Vulnerabilities are the most used form of access, accounting for a shocking 72% of the cases.
Read Blog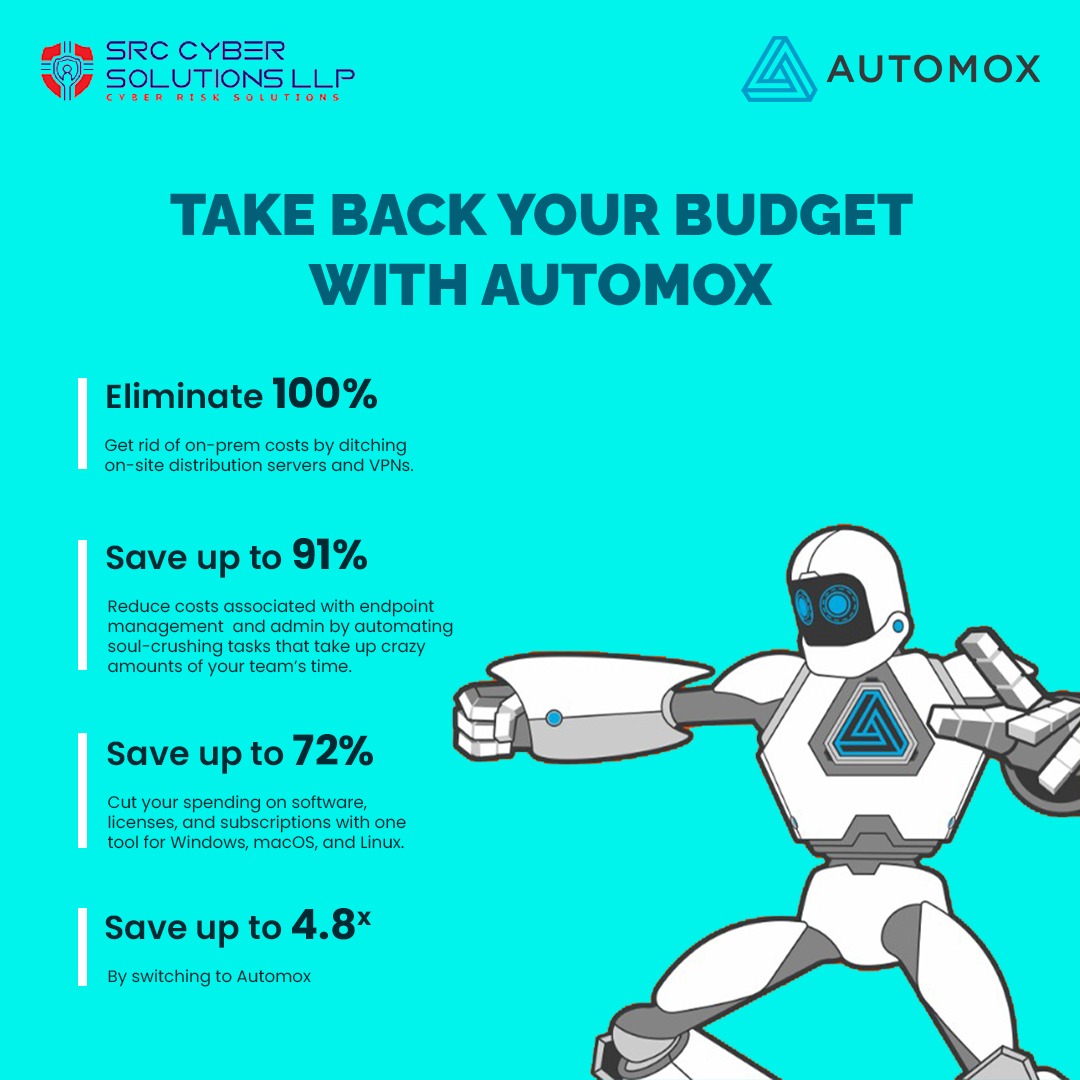
As organizations look to modernize, their #IT environments are more complex than ever before. The quantity and diversity of devices that must be deployed, inventoried, updated, protected, configured, and monitored has skyrocketed as have the number of internal and external threats. The legacy tools still in use by many organizations are complex, costly, and offer limited functionality and visibility.
As organizations look to modernize, their #IT environments are more complex than ever before. The quantity and diversity of devices that must be deployed, inventoried, updated, protected, configured, and monitored has skyrocketed as have the number of internal and external threats. The legacy tools
Read Blog
As organizations look to modernize, their #IT environments are more complex than ever before. The quantity and diversity of devices that must be deployed, inventoried, updated, protected, configured, and monitored has skyrocketed as have the number of internal and external threats. The legacy tools still in use by many organizations are complex, costly, and offer limited functionality and visibility.
As organizations look to modernize, their #IT environments are more complex than ever before. The quantity and diversity of devices that must be deployed, inventoried, updated, protected, configured, and monitored has skyrocketed as have the number of internal and external threats. The legacy tools
Read Blog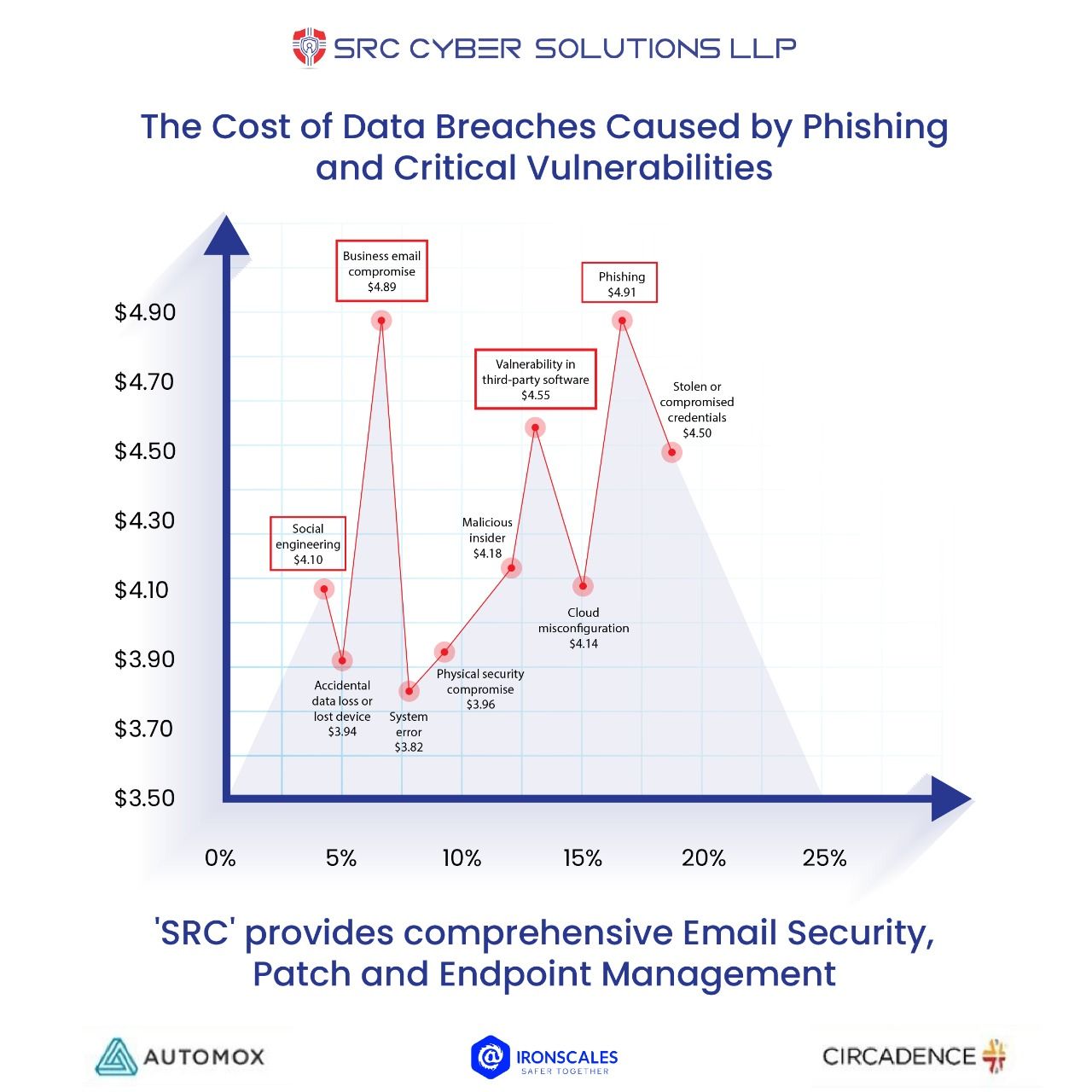
A recent report tabulated the "Costs of a Data Breach" into an Organisation! #Phishing #SocialEngineering and #Vulnerabilities are the most used form of access, accounting for a shocking average cost of US$ 4.60 Million.
A recent report tabulated the "Costs of a Data Breach" into an Organisation! #Phishing #SocialEngineering and #Vulnerabilities are the most used form of access, accounting for a shocking average cost of US$ 4.60 Million.
Read Blog
SRC Garners The Top 10 cyber security solution providers Title in India.
SRC Garners The Top 10 cyber security solution providers Title in India.
Read Blog
Read How SRC Email security & SRC Protects Bhaktivedanta Hospital
No description available.
Read Blog
Learn how IRONSCALES helps to protect Nium against advanced phishing attacks
Learn how IRONSCALES helps to protect Nium against advanced phishing attacks
Read Blog
SRC Cyber Solutions LLP has been found to be of the Quality Management System Standard - ISO 9001:2015
SRC Cyber Solutions LLP is proud to announce that it has achieved the ISO 27001 certification (under number 01 153 062203). The ISO 27001 accreditation is internationally recognized and defines how an Information Security and Risk Management System (ISMS) should be rigorously managed.
Read Blog
SRC Cyber Solutions LLP has been found to be of the Information Security Management System Standard - ISO/IEC 27001:2013
SRC Cyber Solutions LLP, announced today it successfully completed an independent, third-party audit of its ISO 9001:2015 quality procedures and standards for Distribution, Sale, Installation and Technical Support of Information Technology Security Products including Data Security, Data Privacy and
Read Blog
Let's Get To Know Project Ares And Its Importance
Circadence’s Project Ares is an immersive, gamified cyber security learning platform that helps novice and seasoned cyber professionals keep their skills sharp against evolving cyber threats.
Read Blog
Prevent Business Email Compromise Attacks
Leader in self-learning email security becomes the first in anti-phishing to embrace NLP for malicious email classification;
Read Blog
Fake Login Attack Spoof Two Leading Email Delivery Service Providers
IRONSCALES researchers have identified a trending fake login attack spoofing two leading email delivery service providers, Mailgun and SendGrid.
Read Blog
Platform overview, benefits, and insight questions
Project Ares is likened to "the Fortnite" for cyber security learning and training. The hands-on virtual environment puts the fun back into training with gamified elements like scoring and leaderboards.
Read Blog
email security Expands in India
Leaders in self learning email Security technology boasts its international Presence through collaboration with one of India's upcoming cyber- security consultancies.
Read Blog
New Strategic With Circadence
SRC Cyber Solutions LLP announces new strategic partnership with Circadence.
Read Blog
Email Security Expands Threat
Email Security, the pioneer of self-learning email security, today announced another industry’s first with Phishing Emulator™.
Read Blog