Blogs
Explore Automated Patching and Endpoint Management Blogs
Discover how our solutions have empowered organizations to overcome challenges, achieve operational excellence, and drive transformative growth. Learn from real-world success stories.
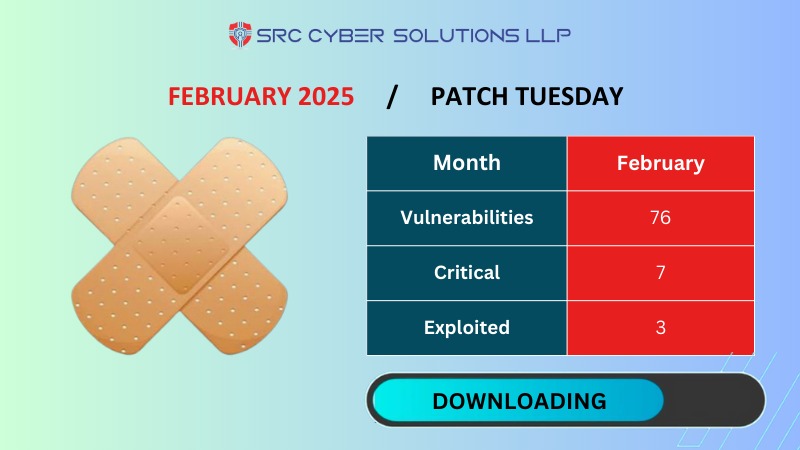
February’s Patch Tuesday Brings 3 Zero-Days and More Woes for Exchange Server Admins
February’s Patch Tuesday is undoubtedly headlined by three zero-days and several important vulnerabilities in Microsoft Exchange Server that allow remote code execution for authenticated attackers. Nothing has been exploited yet, but it’s a fairly safe bet that will be.
Read Blog
IT Ins and Outs for 2025
IT organizations are prioritizing efficiency, security, and adaptability in a fast-paced industry, as usual. But staying competitive not only requires adopting emerging best practices but also moving away from outdated processes. In this blog, you'll get an outline of key IT practices shaping the fu
Read Blog
Becomes an Authorized CVE Numbering Authority
Automox, the cloud-native IT operations platform for modern organizations, today announced its authorization as a CVE (Common Vulnerabilities and Exposures) Numbering Authority (CNA).
Read Blog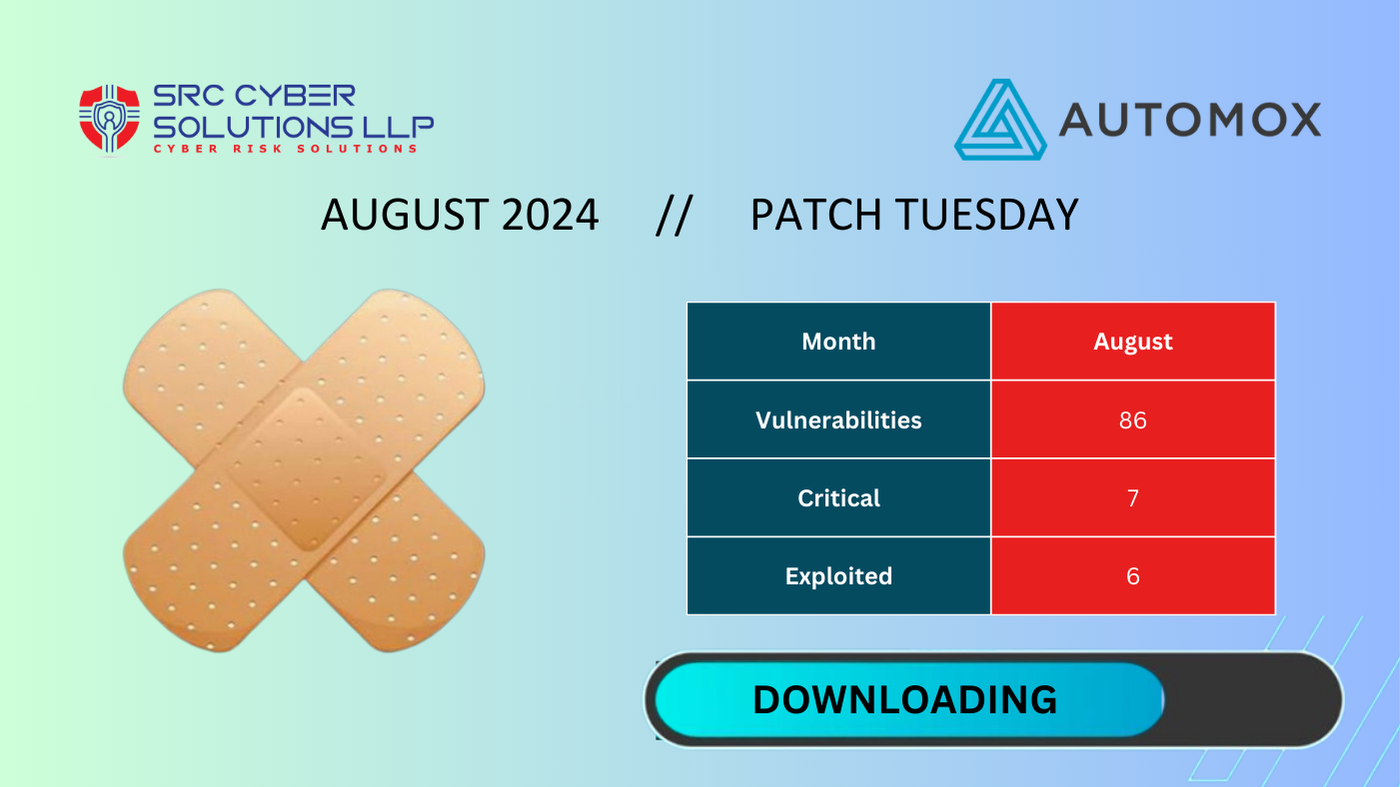
86 New Vulnerabilities: Automox Experts Weigh In
August 2024’s Patch Tuesday has landed and this month we see 86 vulnerabilities and 6 Zero-Days. Among the big bundle of vulnerabilities, you’ll find exploits like CVE 2024-38180, CVE 2024-38133, and CVE 2024-38199. The inclusion of these particular vulnerabilities underscores the need for immedi
Read Blog
Swiftly secure system Update AnyDeskSystem with Automated Patching and remove compromised executables to prioritize digital security.
AnyDesk Software GmbH recently announced their production systems were compromised and that they are revoking code signing certificates prior to AnyDesk Windows version 8.0.8. As a best practice, whenever a code signing certificate is compromised, any executable in your environment signed with that
Read Blog
Automox – Your SaaS Sidekick
As a SaaS provider, you’ve got some pretty big shoes to fill. You’ve got to keep your customers happy and secure while keeping your costs down and staff productive. To help you with that, let’s start by naming three things that are extremely important for SaaS IT teams:
Read Blog
Effortless Efficiency Navigating Endpoint Management with User-friendly Dashboard
Whether you’re navigating a website, submitting an online form, or exploring an app that identifies your newest houseplant, the requirements to deem a tool user-friendly are often the same.
Read Blog
For IT Heroes: Advice for all the Automators
The automation landscape is all about reclaiming your time to focus on meaningful work.
Read Blog
Safeguarding Your Endpoints Made Easy!
Securing your endpoints is important in today’s digital world. Automox worklets provide an ultimate shield against cyber threats, making it easy to protect your digital fortress.
Read Blog
What's in Store for 2024?
With all the IT developments 2023 delivered, it’s clear there’s no stopping change. It really is the only constant. But in IT, we thrive on change. Reflecting on the past year and its major changes, Automox experts are excited to see what the 2024 IT landscape has in store.
Read Blog
Windows - Maintenance Tasks - Remove Old User Profiles
This Worklet removes Windows user profiles older than the provided age threshold
Read Blog
SRC The Real Deal: Automated Vulnerability Detection⇢Remediation
If you’re a sysadmin, it's probably no shocker to read about the pains of vulnerability detection and remediation.
Read Blog
Secure your Linux SSH Connections
Securing your endpoints isn’t just a top priority for IT pros, but also for anyone who takes their online safety seriously.
Read Blog
What is a Security Bypass Vulnerability?
Definition, Impact, and Best Practices for Patching
Read Blog
Boosting IT Productivity: 9 Reasons to Automate Your Patch Management
In the current digital landscape, organizations face the constant challenge of stabilizing security and accelerating the productivity of their IT systems. As such, timely patching is critical.
Read Blog
Making Sense Of Vulnerabilities And Software Weaknesses With CVE, CWE, CVSS, And CWSS
In the infosec world, abbreviations and acronyms abound. But what do they all mean? In this blog post, we'll go over the differences between some commonly confused acronyms – namely, CVE, CWE, CVSS, and CWSS.
Read Blog
For IT, Visibility and Reporting Go Hand-in-Hand
In IT, both phrases ring true. These turns of phrase can conjure feelings of stress when you can’t address your data or view all your endpoints from a single lens.
Read Blog
Automate Patching on Any Endpoint With 5 New Worklets
Our team has been hustling all month to crank out useful Worklets so you can automate any task, on any endpoint. Visit the Worklet Catalog to discover plug-and-play IT automations for hundreds of use cases across Windows, macOS, and Linux devices.
Read Blog
Supercharge Your IT Resources
IT teams need to move faster and faster to keep up with new technologies, stay ahead of vulnerabilities, and drive productivity. Not only that, but having a team large enough to keep up with time consuming day-to-day tasks can be a challenge.
Read Blog
What is a Zero-day Vulnerability?
If you’re in the IT space, you’ll hardly recollect December 2021 as the season for cheer, with the Apache Log4j vulnerability discovery causing shockwaves in the IT community. The finding is perhaps the most well-documented zero-day vulnerability in recent years, with a massive impact vector because
Read Blog
What is the Best Vulnerability and Patch Management Process?
Vulnerability management refers to the process of discovering, identifying, cataloging, remediating, and mitigating vulnerabilities found in software or hardware. Patch management refers to the process of identifying, testing, deploying, and verifying patches for operating systems and applications f
Read Blog
Automated Patch Management for Servers & Workstations
Regular and consistent patching is critical to ensuring every endpoint is up-to-date and compliant with your corporate policies. Speed is also of the essence for patch management to ensure you can secure your endpoints faster than they can be exploited. Finding an efficient way to patch both servers
Read Blog
Cyber Essentials Certification - How Automated Patching and EndPoint Helps with Compliance
The Cyber Essentials and Cyber Essentials Plus certifications are helpful tools for bettering your organisation’s cybersecurity strategy and protecting your IT infrastructure against cyber threats. With automated endpoint management, Automox makes it easy to patch, configure, control, and secure you
Read Blog
Automated Patch Management for Servers & Workstations
Regular and consistent patching is critical to ensuring every endpoint is up-to-date and compliant with your corporate policies. Speed is also of the essence for patch management to ensure you can secure your endpoints faster than they can be exploited. Finding an efficient way to patch both servers
Read Blog
4 Steps to Increase your Trust in Endpoint Automation
We’ve only cleared the first few months of the year, but IT teams are already feeling the heat. With nearly 100 vulnerabilities patched by Microsoft in January and companies worldwide preparing for budget reductions and workforce layoffs, 2023 looks like a tough year for IT admins and IT Operations
Read Blog
If You Work in State and Local Government or Education, the 2023 State of ITOps Report is for You
These are days of limited time and resources. Everything moves so fast and it can be hard for schools or local government organizations to stay on top of ever-changing financial and IT operational landscapes. The 2023 State of IT Operations Survey results indicate that IT operations teams in stat
Read Blog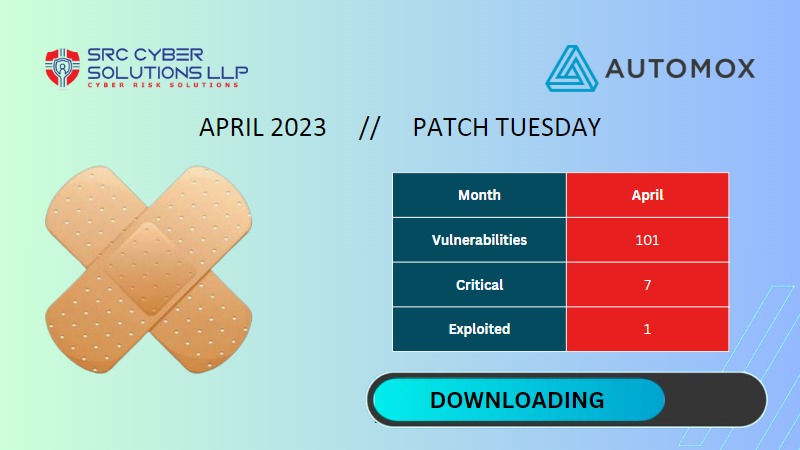
April Sees a Whopping 101 Vulnerabilities Patched
Experts Weigh in on April 2023 Patch Tuesday Release
Read Blog
210+ Titles and Counting: Automated Third-Party Patching
When you’re racing to block bad actors before they can exploit your vulnerabilities, you’ve got to be able to put the proverbial pedal to the metal. When it comes to making sure endpoints are up to date and secure, your organization’s patch efforts shouldn’t be a “when we can get to it” priority. Th
Read Blog
3CX Desktop App Compromised: Here’s What to Do ASAP
We have confirmation that malicious versions of both Windows and macOS of the 3CX Desktop App are being deployed via trojanized updates. However, the application is available for Linux and mobile systems as well. While the desktop applications for those platforms are not known to be compromised, we
Read Blog
Automated Endpoint Patching Checklist
Automation increases IT agility and allows you to simplify IT management in the modern workplace. Over half of IT professionals cite their top three reasons for increasing automation as improved security posture, more control across all endpoints, and reduced cost of IT operations.
Read Blog
What is Use After Free Vulnerability?
If you’re in software development, you may know dynamic memory allocation and management can be a mixed bag. Although memory management within modern software has improved by leaps and bounds, the allocation and release of system memory resources can vary greatly.
Read Blog
4 Steps to Increase your Trust in Endpoint Automation
We’ve only cleared the first few months of the year, but IT teams are already feeling the heat. With nearly 100 vulnerabilities patched by Microsoft this year alone, coupled with companies worldwide preparing for budget reductions and workforce layoffs, 2023 looks like a tough year for IT admins and
Read Blog
Interview with the Experts: Why Automation is the Key to Improving Cyber Resiliency in Uncertain Times
Security teams can feel overwhelmed and disillusioned as they grapple with masses of alerts amid increasing threats from sophisticated cyber attackers. In particular, enterprises that reacted fast in response to global lockdowns need automation to help bolster their security efforts. But there are w
Read Blog
LastPass Breach and Managing Remote Employees. How to stop a similar breach from happening to you
Yet another development has sprung from the recent Lastpass breach saga, this time it’s encryption keys for customer vault backups that were stolen from a Senior DevOps employee, one of only four with
Read Blog
What is the Best Vulnerability and Patch Management Process?
Following vulnerability and patch management, best practices should be a goal for organizations of every size. Vulnerability management refers to the process of discovering, identifying, cataloging, remediating, and mitigating vulnerabilities found in software or hardware, while patch management ref
Read Blog
Cloud Infrastructure 101: Why It's Better and What to Look Out For
The team here at Automox recently shared their predictions for the coming year in 9 IT Trends Set to Rock the Boat. Our thought leaders anticipated that organizations with cloud-based infrastructure would accomplish more with less than on-prem deployments. Where legacy on-prem solutions are fraught
Read Blog
The Lazy Sysadmin: How our platform and OpenAI’s ChatGPT Can Build it, Fix it, and Automate it
If you’re anything like me, you know what needs to be done around the office, so to speak, but can barely find the time to make it all happen. So, we look for tools and resources that can help us get the job done, and even if the outcome isn’t 100% what we envisioned, we still delivered! I’d alwa
Read Blog
How to Create a Centralized Patch Management Strategy in 5 Easy Steps
If you’ve visited this blog before, you know how important patch management is to infrastructure upkeep and security. However, for many teams, developing an effective strategy to deal with outstanding patches can take a back seat to more strategic business matters. The thing is, patch management nee
Read Blog
February’s Patch Tuesday Brings 3 Zero-Days and More Woes for Exchange Server Admins
February’s Patch Tuesday is undoubtedly headlined by three zero-days and several important vulnerabilities in Microsoft Exchange Server that allow remote code execution for authenticated attackers. Nothing has been exploited yet, but it’s a fairly safe bet that will be.
Read Blog
Top 5 Best Practices for Cloud Patching
Over the past several years, modern businesses have been migrating to cloud service providers to take advantage of lower costs, ease of use, and scalability. And according to recent analyst predictions, those trends aren’t changing. To help your team adapt your patching strategy accordingly, we’ve c
Read Blog
How We Worklet: 6 Scripts That Will Change How You Work
Alright, as we make it through the thick of the December holidays, it’s always good to take stock of what you’ve learned, accomplished, and how you can improve your work in the coming days. When we look back on the year, one of the projects we’re most grateful for is our How We Worklet series. Th
Read Blog
Recognition for ‘Easiest Setup,’ ‘Highest User Adoption’ in G2’s Winter Awards
Boulder, Colo., – December 21, 2022 – Automox®, the cloud-native IT operations provider, today announced a series of recognitions from respected third-party software marketplace, G2. Automox received six total awards as part of G2’s Winter 2023 recognition cycle.
Read Blog
Unwrapping Gartner's 7 Rules for Demonstrating the Business Value of IT
IT teams can accelerate their business’s growth by enabling staff to do more with fewer resources. And in today's digital world, organizations must strategize IT initiatives to stay relevant within a landscape of ever-evolving tech. That said, it can be a challenge for teams to reinforce the valu
Read Blog
How to Protect Against Cybersecurity Threats This Holiday Season
The holidays can be a magical time. From Thanksgiving through December each year, there are more reasons to meet friends and family for cocktails or cozy nights in, share time-tested recipes, or tune into any great number of holiday flicks (Love, Actually, Die Hard, The Ref – choose your adventure).
Read Blog
9 IT Trends Set to Rock the Boat in 2023
It’s been a long year, hasn’t it? A long few years, in fact. But we’ve learned a great deal from our most recent challenges. These days, we’re all experts when it comes to changing plans on a dime, adjusting expectations midflight, and recognizing the differences between distraction and more fruitfu
Read Blog
10 Must-have Automation and Operational Tools for 2023
As your organization grows and becomes increasingly multi-faceted, managing the day-to-day operations of business, IT, and security manually can get more and more challenging. If you have limited resources, time, staff, or other limitations, automation and operational tooling help you get more do
Read Blog
What is Authentication Bypass?
Authentication and access controls play a crucial role in web application and system security. If these controls are weak or inconsistent, it can create a vulnerability threat actors can easily exploit via an authentication bypass. What is authentication bypass?
Read Blog
FAQ: How to Implement Together
We’re often asked when Automox is the better choice than WSUS. Of course, we’re biased, so we say ‘always’. But the reality is that some choose to run both WSUS and Automox together, to get the best of both worlds. Here’s what that can look like.
Read Blog
IT Budgeting Checklist
Asking for funding during a financial upswing can be awkward and uncomfortable. Asking for budget in uncertain financial times? Buckle up, it’s going to be a bumpy ride! Use this go-to checklist to cover your bases so your request stands out and gets approved, even when dollars are scarce.
Read Blog
Automated Cross-OS Patching
Automated Cross-OS Patching Say goodbye to manual patching. Automatically patch your Windows, macOs, and Linux devices with one easy to use platform.
Read Blog
PURE CYBER 100: Companies To Watch In 2023
100 cybersecurity startups with $100 million or more in VC funding over the past two years
Read Blog
Advanced IT Troubleshooting
Every single day, IT and helpdesk teams are bombarded with a multitude of tickets. Their goal is generally to keep end users happy and the businesses they work for productive. Typically, this requires a hybrid approach of automation and manual work. Some issues are frequent offenders that can be
Read Blog
5 Things You Probably Didn't Know You Could Automate
Automation brings opportunities galore to IT teams everywhere. And these teams are quickly learning to use automated solutions to manage demand due to staff scarcity and diminishing budgetary resources. IT divisions are also discovering that automation assists with speeding up processes and incre
Read Blog
Gartner’s 2023 Technology Trends Forecast
While many expect 2023 to be all about growth with much of the pandemic and remote workforce expansion behind us, current economic uncertainties, supply chain crises, and a shrinking pool of skilled resources have prioritized trends on which we weren’t focused. We do ourselves a great favor to th
Read Blog
CVEs Then & Now: Is a Cloud Vulnerability Database in our Future?
You’ve heard it before: Sometimes, you have to look back to move forward. From a cybersecurity perspective, this phrase goes a long way when studying Common Vulnerabilities and Exposures (CVEs). CVEs have been a pillar in our industry for decades, but how did we get here, what new trends are d
Read Blog
First OpenSSL Critical Vulnerability Since 2016
Tuesday, October 25, 2022, the OpenSSL project team announced that OpenSSL version 3.0.7 will be released on Tuesday, November 1. The release will include a fix for a critical, security-related vulnerability in OpenSSL versions 3.0 forward. This vulnerability may have existed since September of last
Read Blog
What is Patch Management, Really?
What is patch management? Patch management is the process in which security and/or IT teams identify and apply software or system patches to their organization’s endpoints when new patches or updates become available. Patch management best practices refer to processes and tasks that align with a pr
Read Blog
Tough to Remedy Apache Commons Text Vulnerability
On October 17, 2022, Researcher Alvaro Munoz discovered a vulnerability in the Apache Commons Text. The vulnerability, CVE-2022-42889, is a CVSSv3 9.8 and is present in Apache Common Text 1.5 through 1.9. Proof-of-Concept code walking through the vulnerability is already available.
Read Blog
WLAN Vulnerabilities Discovered in Linux Kernel
Linux Kernel WLAN Remote Code Execution Vulnerabilities On October 13, security researcher Sönke Huster of TU-Darmstadt introduced a POC detailing several CVEs, including CVE-2022-42719 and CVE-2022-42720. Both are remote code execution (RCE) vulnerabilities in the Linux kernel WiFi stack present f
Read Blog
Essential resources to help you tackle your IT operations challenges.
It’s our favorite time of year again – the leaves are changing, the weather is cooling down, and it’s officially Cybersecurity Awareness Month! With a somewhat frightening economic climate, budget cuts, understaffing, and constant news about massive data breaches, the current landscape could be str
Read Blog
5 Steps to Secure Your Hybrid Workforce
As we all start transitioning into post-COVID life, a lot of brainpower is going into figuring out where we should be doing our work. Do organizations stay the course of the past year and fully commit to distributed work (like we did at Automox)? Or request that employees return to the office once i
Read Blog
How to Stay Sane in the Era of Multi-Cloud Infrastructure
In the last year or so, it seems like the wave of companies transitioning their tools to the cloud has skyrocketed, doesn’t it? 92% of enterprises have a multi-cloud strategy. That means that IT teams are left with a buffet of software in different clouds to deploy and maintain. The new world of
Read Blog
2022 Patching & Endpoint Management Checklist - Top 8
What does it take to keep your endpoints configured and secured? Sometimes, this question can seem elusive and you may not always know where to start. To help you get a hold of your security environment and to protect your endpoints in the best way, we’ve created the 2022 Patching & Endpoint Managem
Read Blog
What is Remote Code Execution? Plus how to mitigate or eliminate your exposure
What is remote code execution? Remote code execution (or RCE), often also referred to as arbitrary code execution (or ACE), is a classification of vulnerabilities that allow an attacker to run any command or code on a target system or within a target process. RCE is a top exploitation technique
Read Blog
How We Worklet: Certificate Configuration Assistant
Welcome to the sixth installment of our blog series that focused on the power of automated scripts: How We Worklet. Today, we have the great pleasure of talking shop with Automox Senior Security Engineer, Randall Pipkin. But before we dive in and discover what Randall’s Certificate Configurati
Read Blog
Streamlined Troubleshooting with Remote Control
For teams navigating today’s IT landscape and supporting user device issues, speed and execution of the best-suited resolution are the name of the game. Sometimes, however, these goals can seem at odds with each other. If you’re focused on turning over tickets lightning-fast, things can get overlook
Read Blog
How We Worklet: Python Script to Migrate Policies from Org to Org in Automated Patching and EndPoint Management
Welcome to the fifth installment of our blog series: How We Worklet. Today, we have the great pleasure of talking shop with Automox IT Cloud Engineer, Ryan Braunstein. But before we dive in and discover what Ryan’s Worklet is all about, let’s briefly revisit just what Worklets are and how you
Read Blog
Pros & Cons of Patching with Microsoft WSUS
Windows Server Update Services (WSUS) is a widely used tool that helps administrators with centralized patch management. Distributed by Microsoft, WSUS was designed to alleviate the pain and difficulty of patching manually. For Windows environments, WSUS seemed like a simple solution to the patch
Read Blog
Is There an OS Patching Solution for Windows and macOS?
As networks evolve and department needs change, the PC and workstation market has splintered. While Windows operating systems once dominated, macOS devices have risen steadily. As of June 2022, Microsoft Windows has dominated as the most-used desktop OS worldwide. Microsoft's share of the pie is
Read Blog
Minimizing Threat Exposure Through Automation
It can be difficult to identify gaps in your managed device estate, let alone prioritize vulnerabilities for remediation once they’ve surfaced. Remediating threat exposures often requires coordination across different teams and can be a time-consuming, arduous process. On the second Tuesday of ev
Read Blog
Transforming the Relationship Between ITOps & SecOps
From separate reporting structures, misaligned objectives, and sometimes clashing responsibilities, collaboration across ITOps and SecOps has its challenges. Add to that the remote workforce onslaught and a lack of skilled workers, and you've got a recipe to increase the divide between these essenti
Read Blog
Three ‘Best of’ UEM Awards as Product Momentum Accelerates with IT Troubleshooting
Boulder, Colo., – August 31, 2022 – Automox®, the cloud-native IT operations provider, is the winner of three ‘Best of’ awards from third-party review site, TrustRadius. Automox qualified for the awards in the Summer 2022 Unified Endpoint Management (UEM) software category. Automox was recognize
Read Blog
Beaumont Finally Gets a Good Night’s Sleep
The City of Beaumont’s Information Technology division provides the city’s operating departments with technical support and the software and hardware – from workstations, remote devices, and police car Mobile Digital Communicators (MDCs) – to efficiently deliver services to the public.
Read Blog
Remote Patching Best Practices
There’s no disputing the massive growth in cloud computing and portable devices in recent years. Clearly, industry has moved on in a great many ways from the days of desktop computers and hardwired, on-prem networks.
Read Blog
Sysadmins Lean on IT Automation in Rough Economic Times
When the economy is healthy and things are full steam ahead, it’s easy to fix problems and solve issues with, well, money. In flush times, it’s easier to ask for what you need. But, these are not those times. Today, it seems as though each morning brings more news of downturn. Inflation is ram
Read Blog
How to Protect Healthcare and Pharmaceutical Orgs Against Cyber Threats
The healthcare and pharmaceutical industries are no strangers to cybersecurity threats. In the face of massive global incidents, such as WannaCry and Kaseya, as well as other dangerous, sophisticated attacks, solid security practices are being implemented more effectively. Moreover, executive boards
Read Blog
Analyzing the Economic Benefits of the Cloud-Native Endpoint Management Solution
ESG Economic Validation Report By Aviv Kaufmann, Senior ESG Validation Analyst; and Luz Andrea Vasquez, Consulting Analyst; June 2022 As organizations look to modernize, their IT environments are more complex than ever before. The surface of IT operations has expanded to include the data center, e
Read Blog
What Is Windows Autopatch?
In July of 2022 Microsoft released its new patching service: Windows Autopatch. The Windows Autopatch allows ring deployment-style, automated patch management for Windows 10 and Windows 11. The feature is available to customers with Windows Enterprise E3 and above. It’s no secret that many organi
Read Blog
How Do the Microsoft Tools Work Within Your Ecosystem?
If you’ve been following this blog series so far, you’re aware that we’ve been reviewing Microsoft’s suite of endpoint management tools over the last several months. But to refresh your memory – or if this is your first time joining us – here’s a quick peek at what we’ve reviewed so far: What is
Read Blog
Agent 39 Release Notes
Release Overview Agent 1.0.39 is a minor release that addresses multiple issues.This release is for all supported Windows, Mac and Linux operating systems.
Read Blog
SysAdmins: Tips to Consider When You and Your Workforce Punch the Clock from Home
In many regards, 2022 has been wild so far. However, one pillar of stability seems to be how certain organizations have adopted a remote-work strategy. Initially, the move was a safety measure. But the verdict on remote working is in, and guess what… employees are embracing it. While the buzz abo
Read Blog
Happy SysAdmin Appreciation Day!
It’s the most celebratory of all Fridays – the one, the only: SysAdmin Appreciation Day! At Automox, we love our SysAdmins so much that we held an internal competition to create memes for all the SysAdmins out there. Drumroll, please... Thanks, Katherine Simches!
Read Blog
What is Microsoft Endpoint Manager?
What is Microsoft Endpoint Manager (MEM)? Microsoft Endpoint Manager (MEM) is Microsoft’s Unified Endpoint Manager (UEM). Gartner defines UEMs as “any tool that provides both agent and agentless management of computers and mobile devices through a single console with a user-centric view.” UEMs s
Read Blog
What is Intune?
What is Intune? Intune is Microsoft’s cloud-based mobile device management (MDM) solution. It provides agentless management for devices and is hosted in Azure – which means it doesn’t require on-prem infrastructure nor will it need VPNs to manage devices.
Read Blog
What We Learned from WannaCry 5 years later
What We Learned from WannaCry 5 years later Just over five years ago, on the morning of May 12, 2017, a ransomware attack infected over 230,000 computers in more than 150 different countries. Beyond crippling businesses, the virus spread worldwide – fast – freezing many thousands of public servi
Read Blog
Building Your Business Case: How to Get That New IT Tool Approved
System administrators are usually responsible for the upkeep, configuration, and reliable operation of their company’s IT environment and devices. This often includes uptime, performance, and security. That’s a lot of responsibility. As a system admin, you’re more keenly aware of the technologies
Read Blog
New AXU Course: How to Use API
What is API? The acronym API stands for Application Programming Interface. Simply put, API allows systems to communicate through the delivery of requests and return of output. Automox educator Amelia Vacante offers API insight At Automox University, our goal is to educate your customers quickly
Read Blog
Tetra Defense Reports 57% of Incidents Are Caused by Exploitation of Known Vulnerabilities
Exposed vulnerabilities remain a thorn in the side of IT teams Tetra Defense released its Q1 2022 Incident Response Insights report on June 29, 2022, with findings that attributed 57% of incidents (that Tetra Defense responded to) to an exploitation of a known vulnerability on the victim’s network.
Read Blog
The 2022 State of IT Operations Survey Results Are In
The 2022 State of IT Operations Survey Results Are In Two years ago, most of us got locked out of our offices due to a global health crisis we expected to last mere weeks. But even the darkest clouds have silver linings. Though several businesses initially faced a range of pandemic-specific challen
Read Blog
The Wrap-up: RSAC 2022
What an incredibly rewarding week we shared at RSAC 2022. In a way, this year’s RSAC felt like an industry kick-off event more than a traditional trade show. Seeing connections being made and networks extended was great! This year felt more aggressive than normal in terms of forming new partne
Read Blog
Enable Better Communication and Faster Remediation
In today’s threat landscape, speed is of the essence – especially when dealing with software vulnerabilities and the risk of a breach. This becomes vital when an organization’s SecOps team discovers an exploited, critical vulnerability that their ITOps team must remediate ASAP.
Read Blog
Recap: The 2022 State of IT Operations Survey Report
Two years ago, most of us got locked out of our offices due to a global health crisis we expected to last mere weeks. But even the darkest clouds have silver linings. Though several businesses initially faced a range of pandemic-specific challenges, many have since transitioned into a world that’s e
Read Blog
Detecting Potential Double-Free Vulnerabilities in Ghidra
Ghidra is a powerful tool. Its impressive scripting API can enable researchers to discover potentially vulnerable code within an application they’re testing without relying on long-running and power-intensive fuzzing techniques. In the application security world, continuous testing of your compan
Read Blog
What Is SCCM & How Does It Work?
Microsoft’s SCCM (System Center Configuration Manager, now known formally as Configuration Manager and existing as a branch of Microsoft Endpoint Manager) is a paid lifecycle management solution from Microsoft that keeps track of a network’s inventory, assists in application installation, and deploy
Read Blog
Three Ways to Slash Cost & Complexity in Your IT Organization
How much did you spend on IT last year? And how much more do you plan on spending this year? Technology initiatives have become a top priority for many companies to better prepare for dynamic and complex hybrid workforces. Enhancing infrastructure helps prevent cybercrime and strengthens business
Read Blog
Report: 84% of enterprises struggle to manage their endpoint security
We are excited to bring Transform 2022 back in-person July 19 and virtually July 20 - 28. Join AI and data leaders for insightful talks and exciting networking opportunities. Register today!
Read Blog
Transforming the Relationship Between ITOps & SecOps
From separate reporting structures, misaligned objectives, and sometimes clashing responsibilities, collaboration across ITOps and SecOps has its challenges. Add to that the remote workforce onslaught and a lack of skilled workers, and you've got a recipe to increase the divide between these essenti
Read Blog
The Top 15 Routinely Exploited Vulnerabilities of 2021
Today, the Cybersecurity and Infrastructure Agency (CISA) published a joint advisory with the cybersecurity authorities of the United States, Australia, Canada, New Zealand, and the United Kingdom detailing 2021’s top routinely exploited vulnerabilities.
Read Blog
May 2022 Brings Some Heavy-Hitting Vulnerabilities
This month’s Patch Tuesday looks like a breeze at first glance, but don’t let the numbers fool you! There are some critically important vulnerabilities to get fixed up right away.
Read Blog
Why it’s an “And,” Not an “Or”
If this wasn’t the first thing every Automox MSP customer said to us, it was second or third. And they were right. Their Kaseya or ConnectWise or Intune or NinjaOne or [name your RMM] solution does patching and a whole lot of other things to boot. So…
Read Blog
On-Prem SCCM and WSUS Patch Management Solutions - What Is the True Cost Burden?
Many organizations are caught unaware of the actual cost of their software and solutions. Oftentimes, the sticker price of the software is the assumed cost, but low and behold you get home with your oil-leaking British software to find a host of hidden maintenance costs. Let’s look at Microsoft Syst
Read Blog
Detecting Potential Double Free Vulnerabilities in Ghidra
Ghidra is a powerful tool. Its impressive scripting API can enable researchers to discover potentially vulnerable code within an application they’re testing without relying on long-running and power-intensive fuzzing techniques. In the application security world, continuous testing of your compan
Read Blog
3 Ways to Increase Your Security Posture in Today's Cybersecurity Threat Landscape
Speak with anyone in the cybersecurity field, and they’ll tell you this year will see the highest number of attacks and cybercrime damages to date; speak with anyone next year, and they’ll likely say the same thing. 2022 has seen over 6,000 CVEs reported in its first three months alone, along wit
Read Blog
Expands Partner Ecosystem with Rapid7 and ServiceNow
the cloud-native IT operations provider, today announced new partnerships with Rapid7 (NASDAQ: RPD), who is advancing security with visibility, analytics, and automation delivered through its Insight Platform, and ServiceNow, the leading digital workflow company. The addition of Rapid7 and ServiceNo
Read Blog
How to Fix Vulnerabilities Fast (Starting Now)
No doubt you’ve heard it said that you either do something right or do it fast. Too often, the implication is negative: By increasing speed, you lose accuracy. But in the world of IT, this tradeoff is unacceptable. IT teams need to be fast and precise without affecting the user experience.
Read Blog
How Design Systems Support Rapid Product Development
Design systems are a hot topic. And, lately, they’ve reached the attention of nearly everyone in tech. If the goal is to bring consistency across products, design systems are necessary within software development. But the capability of design systems goes far beyond ensuring product consistency.
Read Blog
How (and Why) to Improve Cyber Resilience
By improving your organization's cyber resilience, you can continue to operate with minimal disruption – even after an attack. Make your plan to avoid disruptions and financial losses.
Read Blog
Apple Patches Its Third Zero-Day In 2022: Webkit Browser Engine Flaw
On Thursday, Apple patched another zero-day, it's third this year after patching CVE-2022-22587 (an arbitrary code execution with kernel privileges vulnerability) and CVE-2022-22594 (a vulnerability allowing users browsing activities to be tracked and identified in real-time) in January. The latest
Read Blog
Patch Now: Adobe Magento Vulnerability Scores a 9.8 out of 10
On Sunday, Adobe released out-of-band updates to patch a critical vulnerability in Adobe Commerce and Magento Open Source. CVE-2022-24086 is an improper input validation flaw that allows an attacker to execute arbitrary code without credentials or administrative privileges.
Read Blog
Patch Now: Samba ‘Fruit’ Vulnerability Allows Remote Code Execution
A new CVSS 9.9 critical vulnerability in the Samba platform allows remote code execution with root privileges. The vulnerability, CVE-2021-44142, is an out-of-bounds heap read/write vulnerability in the Virtual File System (VFS) module called “vfs_fruit”. The vulnerability impacts all versions of Sa
Read Blog
How to Power Remote Workforce Productivity from Within ITOps
The distributed workforce is here to stay. As the dust settles from the transformation of the modern workforce in recent years, no other group is more aware of the shift to remote work, or shares more responsibility for the productivity of this population, than ITOps.
Read Blog
Worklets for Automated Cybersecurity Compliance
Each of these acronyms represents a compliance organization or government regulation that impacts the cybersecurity space in some way.
Read Blog
Unleashes Radical Efficiency for Enterprise and MSP Organizations’ IT Operations
Automox®, the cloud-native IT Operations platform provider, today announced new features to help enterprises and managed services providers (MSPs) manage their large-scale, distributed IT environments with radical efficiency.
Read Blog
5 New Features to Take Advantage Of Automated patching and endpoint management Community
If you’ve visited the Community in the past couple of weeks, you may have seen the new platform, but we’d like to share a just a few of the highlights here.
Read Blog
Why Companies That Prioritize Endpoint Management Will Win in 2022
These are the questions over which IT administrators lose sleep. And, unfortunately, events like Log4J only confirm what most of us already know: We have a massive visibility issue in the IT and security world.
Read Blog
Log4j Exploits in the Wild
As you hopefully know by now, Log4Shell is a zero-day unauthenticated Remote Code Execution (RCE) vulnerability in Log4j versions 2.0-beta9 up to 2.14.1 identified as CVE-2021-44228.
Read Blog
Splunk Plus Drives Insightful Decision-Making
Few people would argue they don’t have access to enough data. It’s easy to suffer from data overload, especially when trying to connect disparate data sources from multiple locations to make business relevance out of it all.
Read Blog
CISA Issues Warning to Patch Your Systems Against State-Sponsored Cyber Threats
A joint Cybersecurity Advisory (CSA) was issued by CISA, the FBI, and the NSA to warn organizations of threats posed by Russian state-sponsored cyber attack operations.
Read Blog