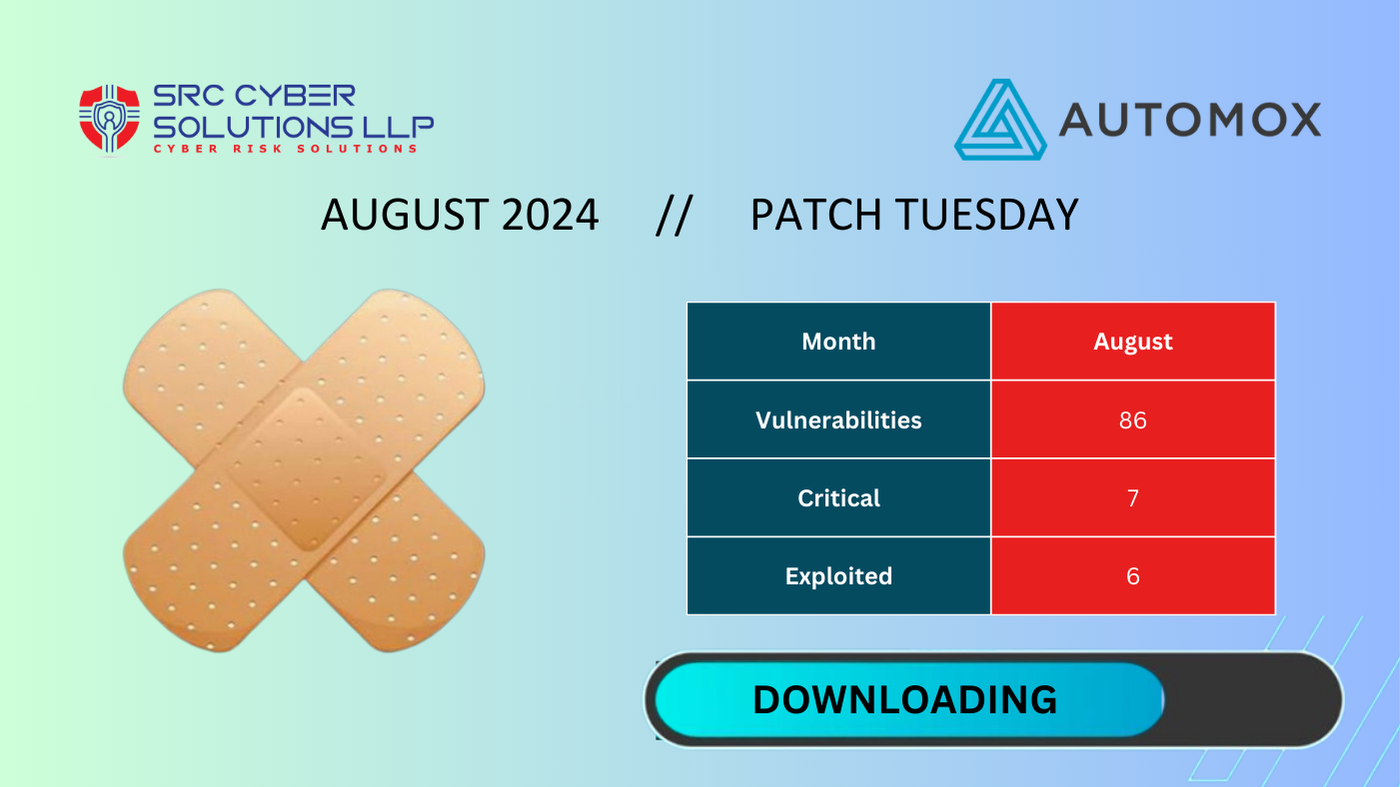
86 New Vulnerabilities: Automox Experts Weigh In
August 2024’s Patch Tuesday has landed and this month we see 86 vulnerabilities and 6 Zero-Days.
Among the big bundle of vulnerabilities, you’ll find exploits like CVE 2024-38180, CVE 2024-38133, and CVE 2024-38199. The inclusion of these particular vulnerabilities underscores the need for immediate patching and proactive security strategies.As usual, we’ve asked a few of our experts to weigh in. For their detailed report, check out the Automox Patch [FIX] Tuesday podcast. There, you’ll get more information and insights into this month's vulnerabilities.
Before we dive into the nitty gritty, however, let’s see how this month's Patch Tuesday stacks up.
CVE 2024-38180 – [Important]
SmartScreen Prompt Remote Code Execution Vulnerability
CVE 2024-38180 is a remote code execution vulnerability affecting Windows SmartScreen prompts. This has a CVSS score of 8.8/10, and should be patched as soon as possible.
Windows SmartScreen serves as a first-line security measure, designed to protect users against phishing attacks, malicious software, and various online threats. By warning users about potentially harmful websites and downloads, SmartScreen significantly reduces the risk of inadvertent exposure to cyber threats. This makes a vulnerability in SmartScreen particularly concerning as it compromises this vital first line of defense.
Common exploit paths for this vulnerability include phishing emails and malicious browser plugins. Since most browser plugins do not require administrative access for installation, they present a significant risk. Educating users about the risks associated with unknown files and emphasizing the importance of verifying the legitimacy of software prompts and emails can greatly reduce the likelihood of successful exploitation.
Understanding the software stack running on your endpoints is critical to maintaining a strong security posture. To mitigate this vulnerability, robust email filtering and browser security measures are key.
Since this vulnerability is actively exploited, immediate action is necessary to secure your endpoints.
– Ryan Braunstein, Team Lead, Security Operations
CVE 2024-38133 – [Important]
Windows Kernel Elevation of Privilege Vulnerability
CVE 2024-38133 (CVSS score of 7.8/10) is a Windows kernel vulnerability that allows attackers to gain elevated privileges on a compromised system. Once exploited, an attacker can execute arbitrary code with system-level access, effectively taking control of the entire system. This can lead to data exfiltration, system corruption, and further network penetration.
This vulnerability can be exploited through phishing emails, malicious executables, shady web pages, and drive-by downloads. Attackers can trick users into connecting to a malicious server, allowing them to download and execute arbitrary code, ultimately gaining kernel-level access to the system.
User training is many times the best defense in preventing such exploits. Educate your users on recognizing phishing attempts and avoiding interactions with malicious content. In addition to user training, hardening your systems by regularly updating your operating systems, applying security patches, and implementing advanced endpoint detection and response (EDR) solutions can help detect and mitigate threats before they escalate.
– Seth Hoyt, Senior Security Engineer
CVE-2024-38199 – [Important]
Windows Line Printer Daemon (LPD) Service Remote Code Execution Vulnerability
Printer service vulnerabilities can pose significant threats, especially to legacy systems that rely on outdated technology and lack modern security measures. These older systems often run obsolete software versions that are no longer supported or updated, making them prime targets for attackers.
CVE 2024-38199 was rated with a CVSS score of 9.8/10.
Legacy systems, which may still rely on older versions of these services (LPD), are particularly vulnerable because they do not benefit from the latest security patches and updates.
One concerning aspect of printer service vulnerabilities is their potential to enable 'sit and wait' attacks. Since these legacy systems are often left unattended, attackers gain access to a system and then lie in wait, undetected, for extended periods.
The passive nature of these attacks makes them especially dangerous, as they can go unnoticed by traditional security measures that focus on immediate threats and anomalies. In legacy systems, the lack of advanced monitoring tools further exacerbates this risk, providing attackers with ample time to fully exploit the vulnerability.
Implementing robust network segmentation and up-to-date endpoint protection measures can also help contain potential threats and prevent attackers from moving laterally within a network.
Regular security audits and health checks can identify any outdated services or configurations. In today's threat landscape, maintaining a proactive security posture is essential to safeguarding against persistent and emerging vulnerabilities.
– David van Heerden, Technical Product Marketing Manager
Patch Regularly, Patch Often
Consistent patching is your first line of defense against vulnerabilities. Regular updates ensure that your systems are protected against the latest threats.
Staying vigilant and proactive in your patch management strategy can prevent many security incidents before they occur. Make patching a routine part of your IT operations to maintain a secure and resilient infrastructure.
Remember, the effort you invest in patching today can save you from significant security breaches tomorrow. Prioritize updates and educate your teams on the importance of timely patch management.
Until next time: Patch Regularly, Patch Often.