Sometimes I hear the following from security professionals when we talk about their awareness program:
"We are averaging a 2-3% click rate on our phishing simulation program; we are in a great place!”
My immediate answer is: “How difficult are your phishing templates?”
As the conversation unfolds, I get to learn more about their programs, and many times I would hear the same practices repeating themselves, practices which I believe provide organizations with a false sense of security and readiness to deal with the high sophistication level of phishing email and social engineering scams these days.
At the end of the day, it all boils down to the fact that they are making their awareness program too easy for too long! But not on purpose, as they are limited by their tools and the kind of templates at hand.
3 Steps to Lowering Your Phishing Click Rate
Start Easy
It is totally OK to start with easy. I would even argue that you MUST start easy, tailoring the level of phish to the awareness level of your employees as you go along.
If you don’t have a good tool, check out our free phishing simulation and Training tool, Starter, to get your organization accustomed to the concept of ongoing phishing exercises.
Choose a Phishing Template
Selecting a phishing template can be difficult, even when you have a pre-populated list/bank of suggested templates.
There is a lot of guesswork involved in the process of picking up the right template and training. The most important thing to remember is that it is easier to identify a bad template than it is to find the right one.
So, what makes a phishing campaign bad or easy to identify?
- Clear coverups – making an attempt to appear like the email is from a known vendor but changing the name to avoid copyright infringement.
- Not investing the time to make it right for your organization: Sender name and address; Internal language; Stylometry – any specific tags, signatures, postfix, or prefixes you add to your external/internal emails?; Timing – when do this kind of messages normally hit your mailboxes?
- Not following up with immediate feedback on the obvious hints inside the phishing email the targeted users should have picked up on.
Launching a bad or easily identifiable campaign can cause more damage than good. It is harmful, not just because they give us the false sense of achievement, but they are also sending the wrong message to the users that phishing is easy to spot! When we know it’s not.
Measure Click Rate
Finding the true click rate is tricky. Although some vendors offer benchmarks, it is hard to find a one-size-fits-all solution since different companies are in different places in their program and journey, and it is hard to make comparisons.
If you feel that you are advanced in your program (most of your employees have gone through 6 different scenarios), try the next template and expect the following:
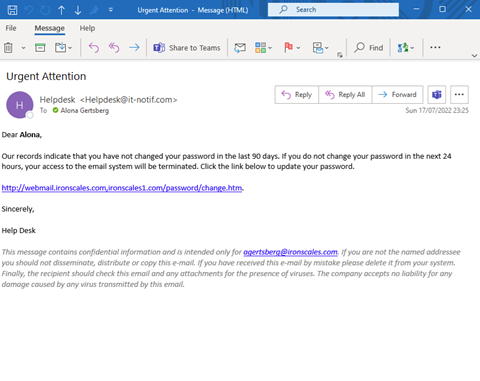
- Avg click rate 18% (you are doing OK)
- Best click rate 1% (you are killing it)
- Worst click rate 93% (There is some more work to do here)
