
OT Device Security Through Physical Layer Visibility
The First Industrial Revolution began in the 18th century. Today, as technology evolves even more, we are experiencing the Fourth Industrial Revolution – also known as Industry 4.0. This most recent revolution involves the application of IT technology to industry; in short, it is the convergence of IT and OT. These cyberphysical systems (CPS) encompass the Industrial Internet of Things (IIoT), in which OT is controlled and monitored by smart devices in order to improve efficiency and accessibility.
However, despite bringing significant benefits, IT/OT convergence exacerbates the cybersecurity risk; blending these once idiosyncratic environments means IT incidents can affect OT. And attacks on OT – deliberate or not – are much more severe as the consequences permeate into the physical world.
OT Device Security – Hit them where it hurts
Critical infrastructure relies on OT, and we, as nations, rely on critical infrastructure for national security. Hence, the continuous operability of OT is essential to maintaining national security. Such dependency makes OT assets an extremely valuable target, a target that has become more accessible since converging with IT. The increased vulnerability is very worrying as any OT downtime causes subsequent disruptions to critical infrastructure… Recent incidents, such as the attacks on Colonial Pipeline and JBS Foods, served as reminders – to both victims and perpetrators – of the threat to national security that attacks on critical infrastructure have.
OT often gets hit with ransomware, due to its disruptive nature. There are several bad actors with differing motives whom would wish to sabotage OT environments. One such player is state-sponsored groups, who seek to undermine an adversary’s national security to advance their agenda. Cyberwarfare is becoming an increasingly viable tactic for such purposes, with nation-backed actors possessing sophisticated resources that allow for highly disruptive attacks on critical infrastructure. Terrorist organizations are other threat actors who view OT as a prime target.
With real-world consequences, 45% of which put physical safety at risk (an increase of 6% from the previous year), OT disruptions cause society to feel vulnerable and, in turn, doubtful of the government’s ability to uphold national security. While not necessarily causing any fatalities (although such a scenario is not impossible), the attack still achieves the underlying goal of terrorism: generating widespread fear and irrational reactions. Financially motivated cybercriminals, too, see value in attacking OT. Critical infrastructure entities have zero tolerance for downtime and are, thus, highly incentivized to give in to monetary demands to resume operations.

IT/OT convergence provides an open invitation
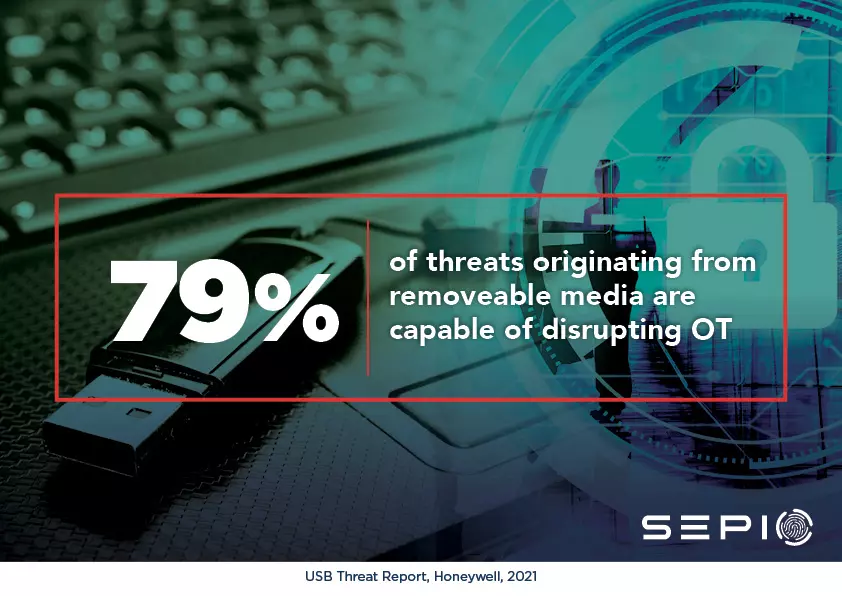
As mentioned, Industry 4.0 has made OT more accessible. Due to the interconnectedness between IT and OT, the former can provide a gateway to the latter, or an attack on the IT environment can impact the OT environment – intentionally or not. Hardware-based attacks are one such threat taking advantage of IT/OT convergence. Rogue devices, the tools used in hardware-based attacks, require physical access, and the countless endpoints in the IT environment all act as an entry point to OT. Worryingly, research by Honeywell found that 79% of threats originating from removeable media are capable of disrupting OT.
Moreover, rogue devices bypass existing security controls, such as NAC, IDS, and IoT Network Security, by exploiting the lack of Layer 1 visibility; spoofing devices and hidden implants go undetected, undermining even the most stringent of security controls. A recent study by ESET found that 100% of attacks compromising air-gapped networks did so using a weaponized USB device. Of course, IT/OT convergence has seen a decline in air-gapping as the two contradict each another. However, even Zero Trust, which is often relied on as a robust defense mechanism against the cybersecurity risks associated with Industry 4.0, is insufficient in defending against hardware-based attacks. By exploiting the Layer 1 blind spot, rogue devices manipulate access controls to gain network access, move laterally, and circumvent microsegmentation policies.
Get Professional OT Device Security with Sepio’s Solution
Ultimately, the challenge associated with hardware-based attacks on OT is the lack of visibility; security controls and policy enforcement are ineffective if an enterprise doesn’t know what devices are operating in its infrastructure. Sepio’s asset risk management solution provides a panacea to the gap in visibility by covering Layer 1, (the Physical Layer), offering complete asset visibility. By going deeper than any other solution, Sepio’s Layer 1 visibility means no device goes unmanaged; the solution identifies, detects, and handles all IT/OT/IoT devices. Such visibility supports the solution’s policy enforcement mechanism and Rogue Device Mitigation feature, in which Sepio instantly detects any unapproved or rogue hardware, blocking such devices through an automated mitigation process carried out by third-party tools. The Zero Trust Hardware Access approach provides protection at the first line of defense and prevents Zero Trust security protocols from getting bypassed.
HAC-1 requires no hardware resources and does not monitor any traffic; within 24 hours, we can provide you with complete asset visibility and identify previously undetected rogue or vulnerable devices. With national security at risk, critical infrastructure providers must do all they can to prevent harmful attacks. Don’t wait for the symptoms; get to the root cause of the problem with HAC-1.