Product Release Notes v51.00.00

With the v51.00.00 release of IRONSCALES, we are pleased to announce the following product improvements and new features:
Report Phishing button for Office 365 shared mailboxes
We're pleased to announce that the Microsoft Report Phishing add-on (OWA) now works with Office 365 shared mailboxes, allowing your organization's users to report suspicious emails in their shared mailbox/folder. No more "please forward to 911" workarounds are necessary.
Note: No additional configurations are needed if you deployed the Report Phishing add-on before November 2021. To verify it works, access a shared mailbox in your Outlook Desktop App (not on the web) and make sure you see the Report Phishing button on the mailbox's emails. If it is missing, redeploy the add-on.
Improved auto-remediation for Spam incidents
We've made improvements to IRONSCALES' ability to automatically remediate Spam incidents. Your SOC analysts spend long hours safeguarding your organization and with this recent upgrade, they will need to spend less time investigating and manually remediating Spam incidents.
Protect only synced mailboxes in Microsoft Teams
To avoid accessing data of unprotected users, IRONSCALES only runs link and attachment scans on messages in chats that have at least one protected mailbox. Note that since blocking is done on the message level and not on the user level, we will also block messages for unprotected users in chats with a protected mailbox.
Allow sending campaigns over the weekends from the campaign's setup
Campaign designers can now control whether their campaigns will run on workdays (for example, Monday-Friday) or throughout the entire week, including weekends (entire week by default). This is done from the Campaign Setup form and overrides (for the specific campaign) the business days selection in the General & Security settings page.
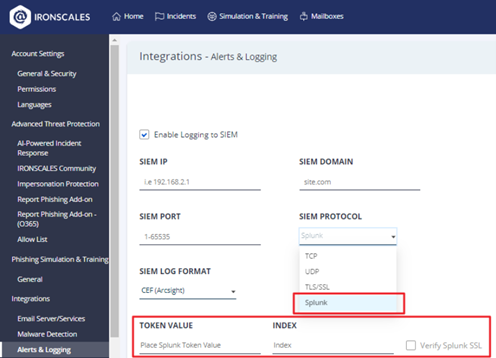
Support for SIEM integration with Splunk Cloud
IRONSCALES now supports using Splunk Cloud for storing and managing IRONSCALES alerts and logs. For details, see SIEM.
Outlook MSI Reporting Add-on Expires May 11th, 2022
The Outlook MSI Reporting Add-on's certificate expired on May 11th and needs to be updated. The new version (3.2.7) of the add-on is available for download from the Resources page. For details, see Outlook MSI Reporting Add-on Expires May 11th, 2022.
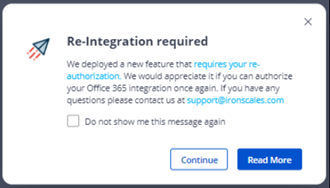
Present reintegration notification for ATO/Teams Customers (O365 users only)
Existing customers, who integrated their Office 365 account prior to the release of Account Takeover and Microsoft Teams Protection support, do not have these capabilities active. However, many customers do not even know they need to reintegrate their O365 account to enjoy these features. So, if you are entitled to use either or both features and need to reintegrate, the next time you log into IRONSCALES you will see a popup window, prompting you to reintegrate.
We provides a SelfLearning NexGen User-Friendly platform combining AI and HumanInsights (HI) along with providing a number of advanced detection techniques for such Impersonation attempts, Polymorphic Attacks, Phishing, Fake Login, SocialEngineering, AccountTakeover, and URLs Links detection using ComputerVision Technology, 50+ engines scanning for advance MalwareDetection BEC Anomaly Detection using Natural Language Processing and offers a multi-layered approach, all combined with our Award Winning MLearning and AI-powered IncidentResponse and Virtual SOC remediating these attacks at the Mailbox level. SRC Cyber Solutions LLP in India provides the most comprehensive Mailbox Level Protection. If you want to know more kindly Click here

