Product Release Notes v62.00.00

The 62.00.00 release of IRONSCALES includes several Simulation & Training, and Incident Management enhancements, as well as some bug fixes.
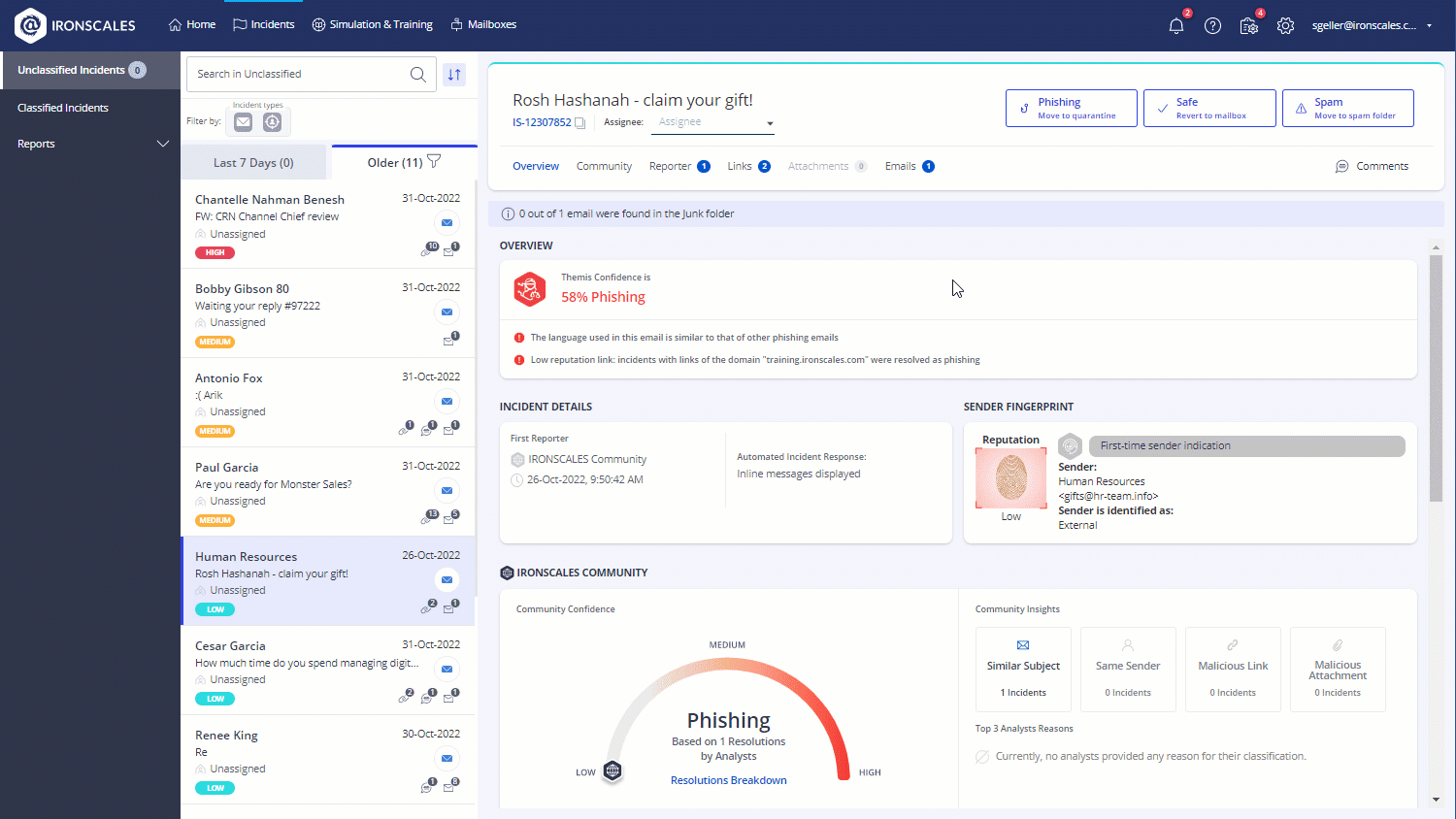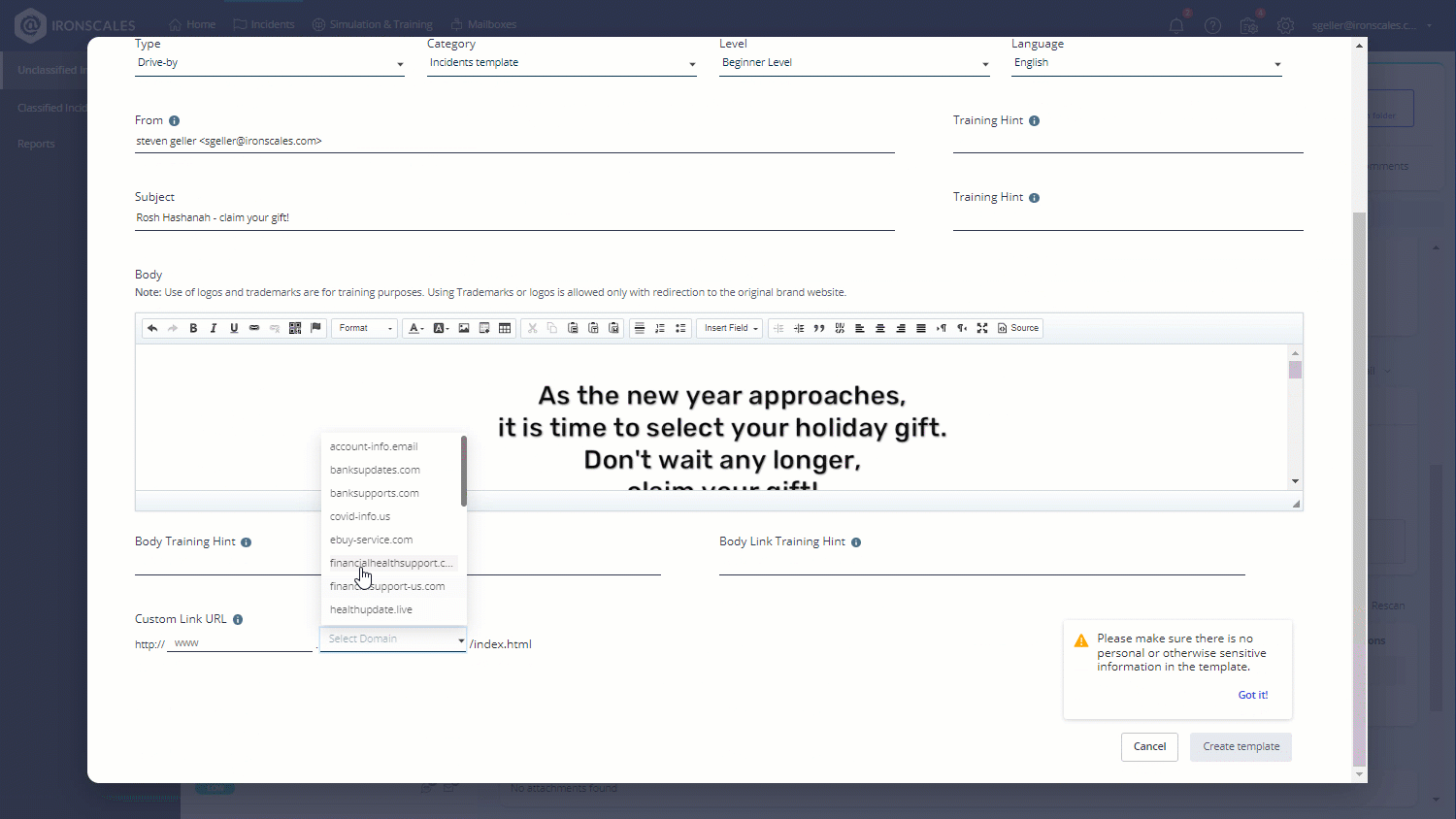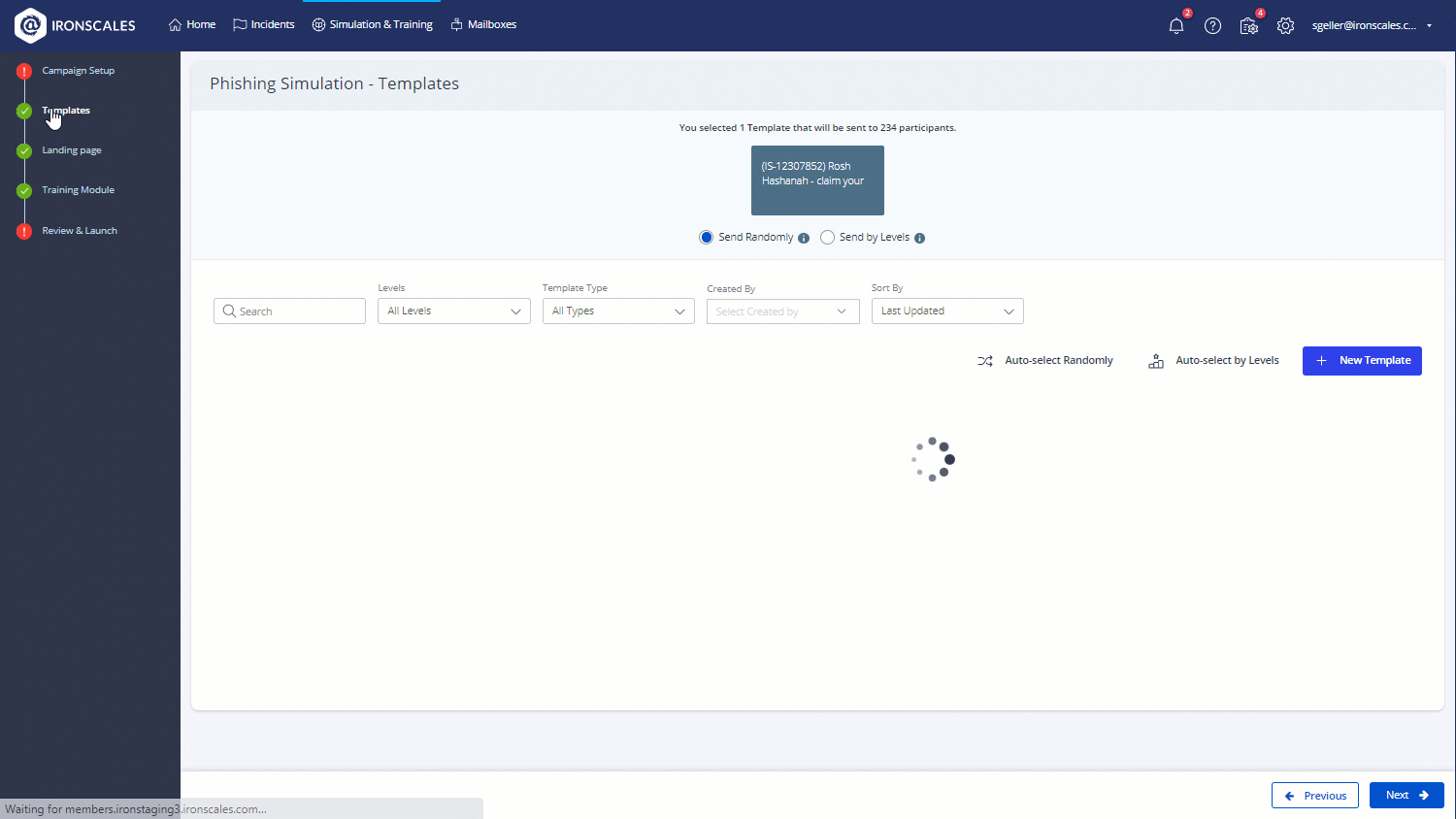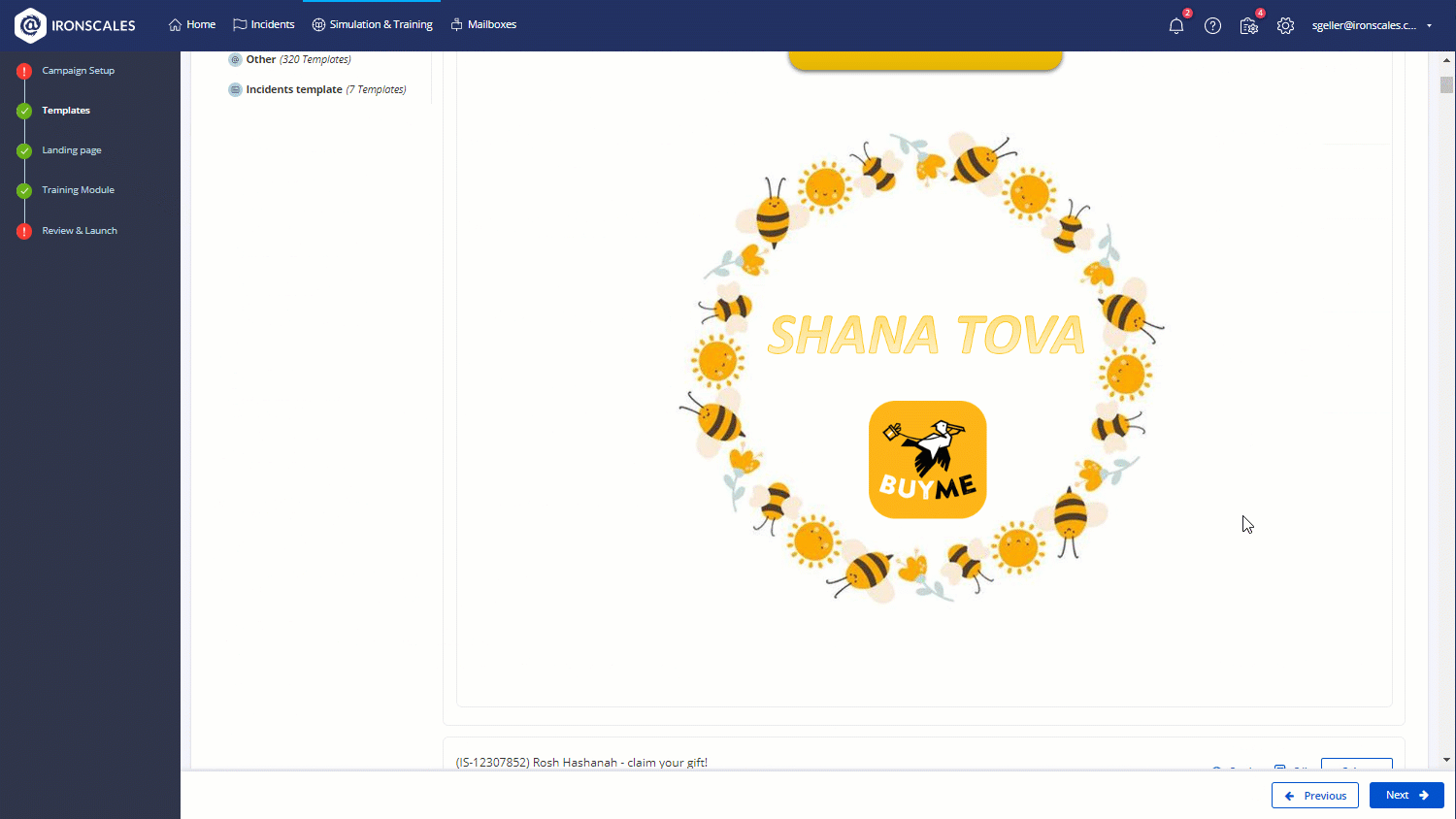
Create templates from threats
Save time and quickly send out campaigns based on the latest phishing incidents!
Utilizing our unique machine-learning capabilities, you can now create campaign templates out of email incidents, allowing you to quickly and easily raise your organization's awareness for the phishing attacks that are targeting your users.
Supported for classified, unclassified, and 90-day scan back incidents, the new templates are created either as Drive-by or Attachment templates based on the incident's contents and predefined with the incident's subject and number and a default category (Incidents template).
- As an IRONSCALES admin, in the incident's details, click Create Template.
- In the From field, enter the sender.
- Update the body and Subject of the template.
- Specify the link or attachment URL as appropriate.
- Remove any sensitive information or malicious content.
- Click Create template.
Here's a short video showing the process:
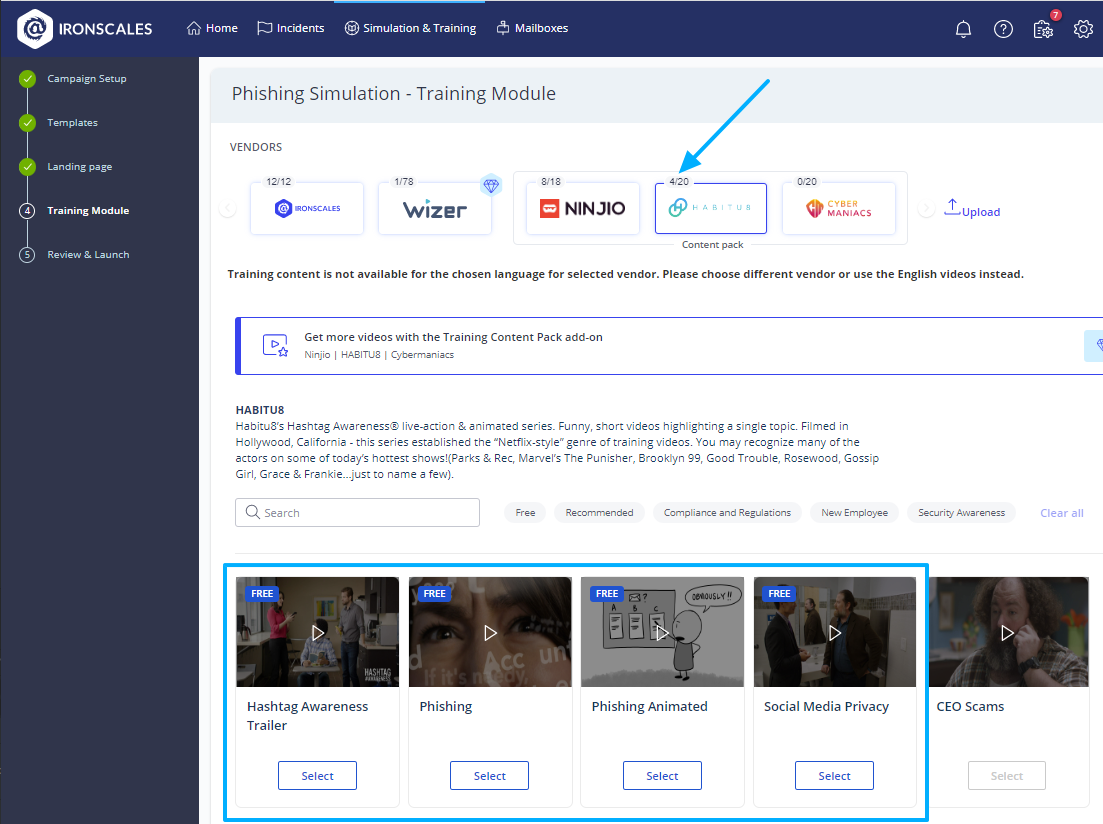
Campaign 'Training Module' screen - display enhancements
You may not know this, but you're entitled to free training videos from our different content publishers even if you haven't purchased the Phishing Simulation Content Pack. So, to make it easier for you to find the content you're looking for, in the Training Module screen of the campaign setup wizard, we've added an indication to each content publisher of the number of available videos out of the total. In addition, the videos you're entitled to use are conveniently displayed at the top of the screen.
New and improved 'Sender Fingerprint' overview
This is part of a wider initiative focused on improving the display and content of IRONSCALES incidents.
The new and improved Sender Fingerprint overview is here, allowing security analysts to quickly identify anomalies and accurately classify incidents.
The first thing you'll notice is the new look of the section, divided into four subsections: Sender, Sender Domain, Mail Server, and Return Path, each displaying the relevant details.
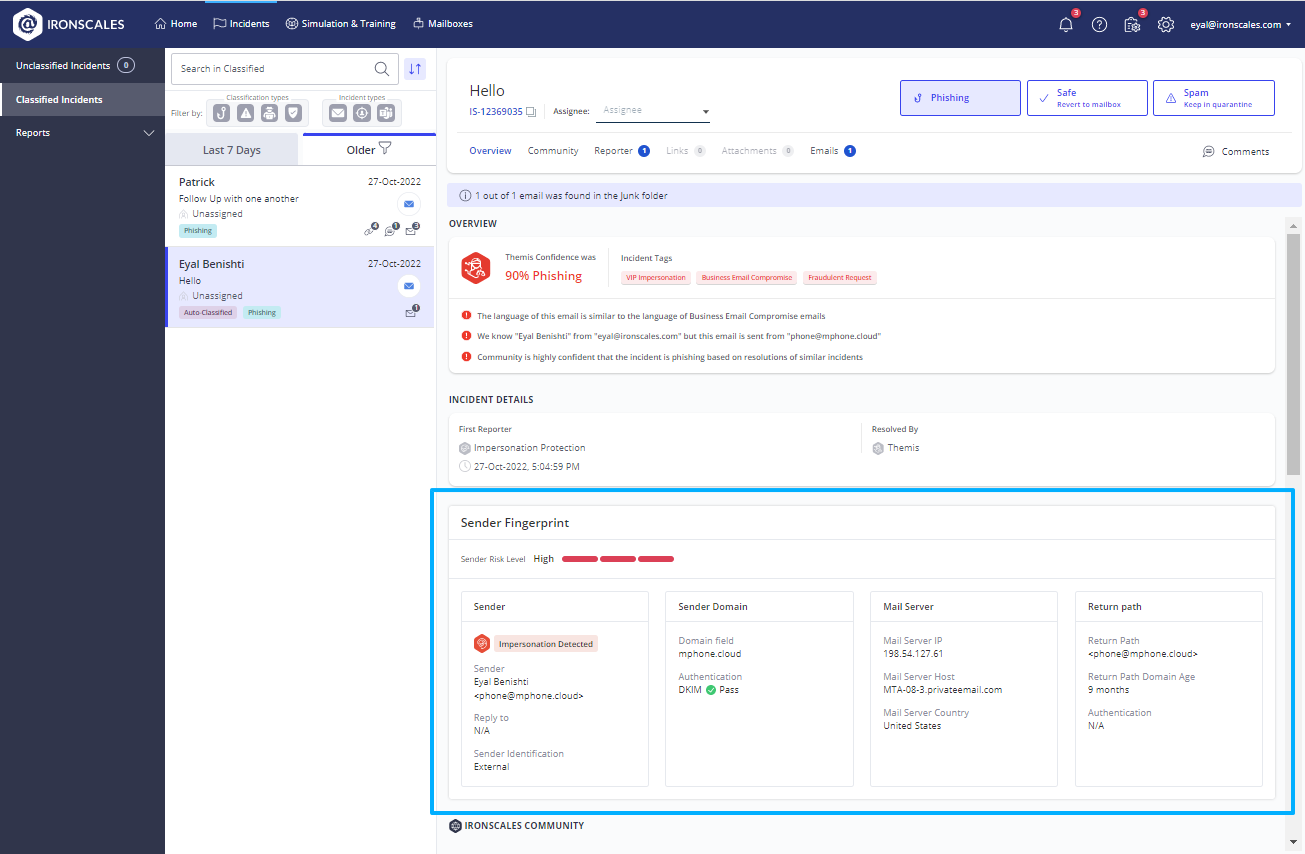
The section now presents additional details, including:
- The sender's reputation was replaced with the more intuitive Sender Risk Level (Low, Medium, High)
- IRONSCALES banners attached to the email (First Time Sender, Impersonation attempt)
- Relevant authentication method (SPF, DKIM, DMARC)
- Sender identification (Internal, External)
Improved automatic detection and classification
We are pleased to announce that we have significantly strengthened our Detection and Classification capabilities in the EU environment by approximately 20%. We are confident that this update will greatly enhance our machine-learning prowess to protect against potential security breaches, ensuring the continued safety and security of our EU customers.
Automatic classification of spam-only incidents
To save your SOC analysts' time and help them focus on the more pressing phishing threats, IRONSCALES will auto-classify incidents (as Spam) if all of the incident's emails are in the Spam folder 1 hour after the incident is created. The idea is to wait an hour to allow our clustering mechanism to add additional related emails to the incident.
Reach out to your Customer Success Manager if you would like to have this feature disabled.
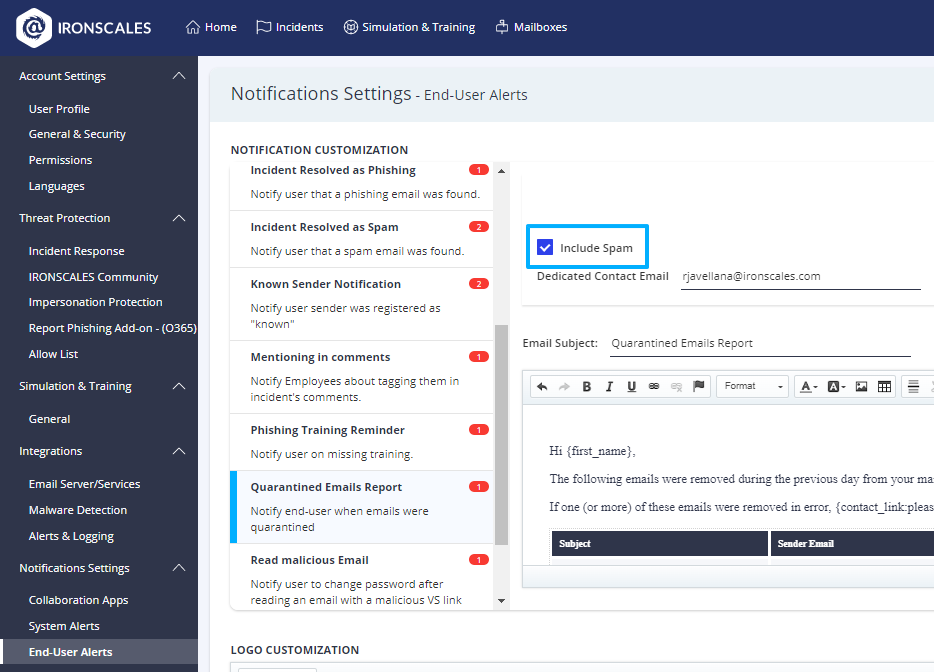
Option to exclude Spam emails from the 'Quarantined Emails Report'
Following customer requests, we have added an option to exclude spam emails from the Quarantined Email Report, allowing your end-users to focus on the emails that were entirely removed from their mailboxes. The report has traditionally included emails from both Spam and Phishing incidents, which remains the default behavior. To exclude spam emails from the report, in the End-User Alerts settings page, clear the new Include Spam checkbox from the report and click Update.
We provides a SelfLearning NexGen User-Friendly platform combining AI and HumanInsights (HI) along with providing a number of advanced detection techniques for such Impersonation attempts, Polymorphic Attacks, Phishing, Fake Login, SocialEngineering, AccountTakeover, and URLs Links detection using ComputerVision Technology, 50+ engines scanning for advance MalwareDetection BEC Anomaly Detection using Natural Language Processing and offers a multi-layered approach, all combined with our Award Winning MLearning and AI-powered IncidentResponse and Virtual SOC remediating these attacks at the Mailbox level. SRC Cyber Solutions LLP in India provides the most comprehensive Mailbox Level Protection. If you want to know more kindly Click here

