- 25-Jul-2024
Data Catalogs: What They Are & Why They’re Important
This blog explains what data catalogs are and why they are an important investment

Follow along for product updates, threat research, and strategies for overcoming the challenges of modern security teams.

This blog explains what data catalogs are and why they are an important investment

Open source security is a term used to describe the process of protecting your organization’s data and network from attack by using open-source software. It refers to the use of open-source software (OSS) for data protection. Open source software is free to use, meaning that anyone can access it wit
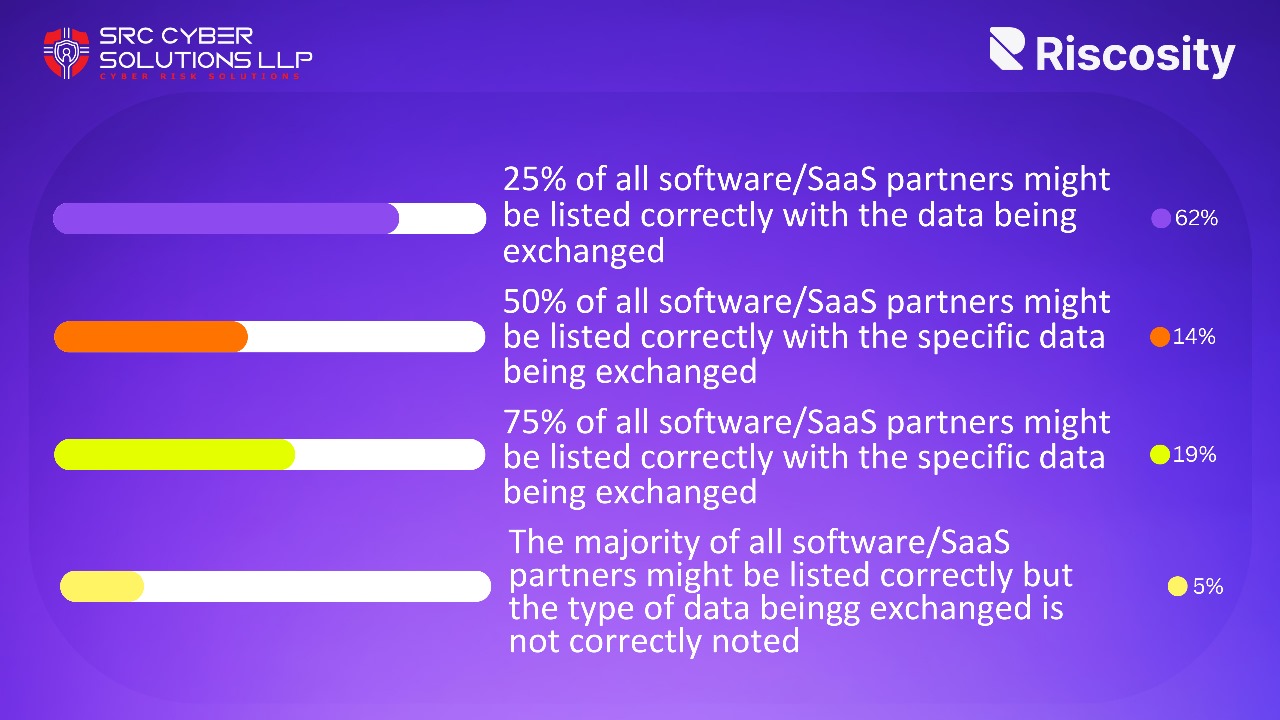
Keeping a Pulse on All Third-Party Connections One of the main goals of information security is to protect assets. Security Guest Expert Security Expert Published on 1/17/2024 5min. A blog image for the how to respond to the MOVEit attack blog. The core tenets of information security i

A comprehensive application risk assessment guide sharing tips and considerations of the process of evaluating and understanding the security risks associated with an application.

Data lineage and data provenance are related terms, but different. Lineage focuses on the origins and movements of data over time, while provenance focuses on the transformations and derivations of data from original sources. Provenance helps teams to follow the source of data and verify its authent

A policy, by definition, is a statement of management intent that is mandatory for an organization.
© 2024 SRC Cyber Solutions LLP. All Rights Reserved.