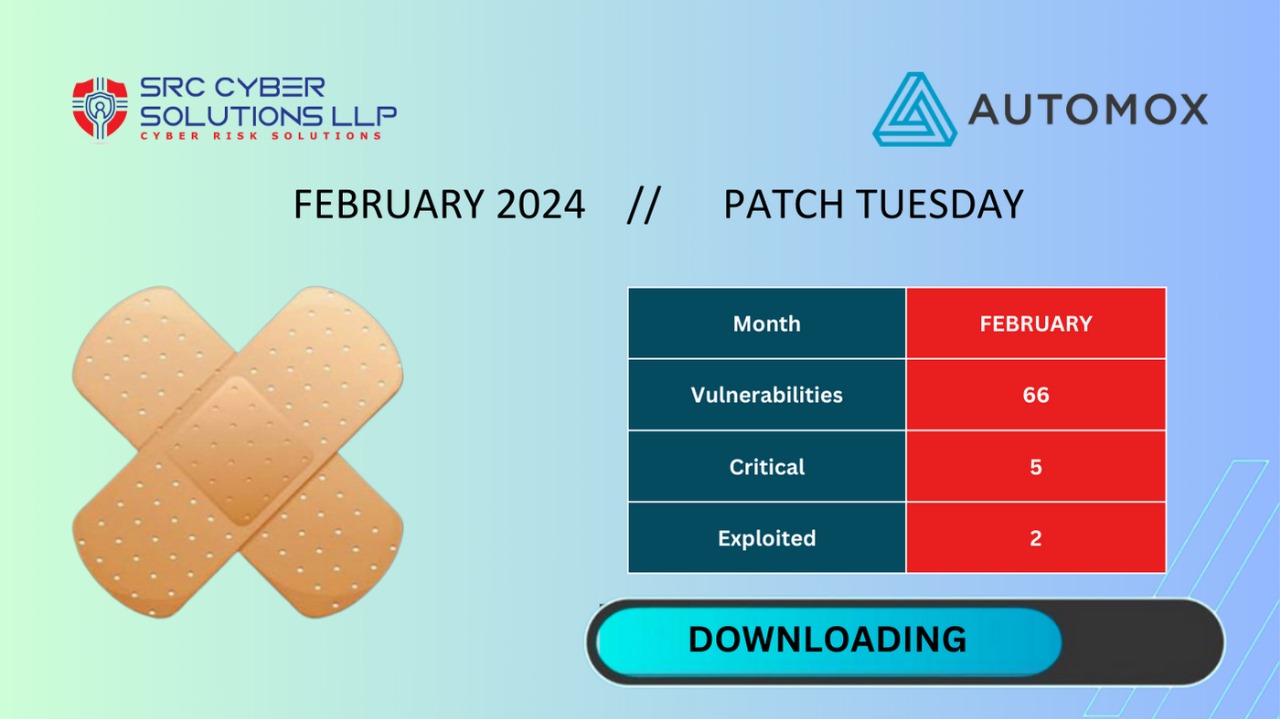
February Patch Tuesday: 73 Vulnerabilities and 2 Zero-Days
As February’s Patch Tuesday rolls around, IT teams face the familiar drill of updating and securing their systems.
This month’s update bundle shines a spotlight on the need for businesses to develop their automation maturity. Efficiently addressing vulnerabilities – especially as part of a well-structured automation strategy – can dramatically reduce the window of exposure and the workload for IT teams.
With 73 vulnerabilities released this Patch Tuesday, let’s dive into some of the more critical vulnerabilities and understand why prompt, automated responses are more crucial than ever.
CVE-2024-21401
Microsoft Entra Jira Single-Sign-On Plugin Elevation of Privilege Vulnerability [Important]
A particularly concerning issue this month is CVE-2024-2140, which affects the Microsoft Entra Jira Single-Sign-On Plugin. This elevation of privilege vulnerability could allow an unauthenticated attacker to manipulate the plugin's configuration, leading to unauthorized access.
To protect against this flaw, manual update procedures to the latest version are essential, but the conversation in the cybersecurity community hints at the growing number of honeypot Jira instances out there. These systems, designed to attract and monitor malevolent actors, underscore the heightened attention needed for plugins and third-party integrations — a task significantly streamlined through the implementation of effective automation.
- Tom Bowyer, Director IT Security, Automox
CVE-2024-21351
Windows SmartScreen Security Feature Bypass Vulnerability [Moderate]
Another flaw that has emerged is CVE-2024-21351, a security feature bypass vulnerability in Windows SmartScreen. This technology is a critical first line of defense against downloaded internet files that might carry malicious payloads.
It's been revealed that an attacker could potentially bypass this check to execute untrusted files without prompting the user — a clear-cut reminder of the vital role SmartScreen and similar protective measures play in maintaining system integrity.
The bypass of such a critical security component can lead to substantial data breaches and increase the risk of subsequent malicious activities, making the swift identification, reporting, and patching of such vulnerabilities a top priority for maintaining cybersecurity.
- Seth Hoyt, Senior Security Engineer
CVE-2024-23218
CoreCrypto
While it is Microsoft’s Patch Tuesday, we’d be remiss if we didn’t mention CVE-2024-23218, a weakness within macOS Sonoma's CoreCrypto framework. This timing side-channel issue, while technical in nature, represents a loophole that allows attackers to decrypt RSA PKCS#1 v1.5 ciphertexts without the required private key.
Despite advancements in secure communications, CVE-2024-23218 is a stark reminder of the persistent issues associated with legacy cryptography standards. RSA PKCS#1 v1.5 dates back to the early 90s and has been deprecated for quite some time.
This vulnerability underlines the risks of relying on outdated technology that may not stand up to modern cryptographic analysis and advanced attack methods. While a deprecated cryptographic method should no longer be in use, a patch for it is still a priority. I wouldn’t want to find out the hard way that something still relied on it.
- Jason Kikta, CISO / SVP of Product, Automox
Robust automation aids your Patch Tuesday efforts
This Patch Tuesday, as with all others, serves as a reminder for organizations to constantly evaluate and improve their patch management strategies. Creating a robust automation framework can address vulnerabilities efficiently, reduce manual oversight, and mitigate risks in an ever-evolving threat landscape.
As we continue to see from these patches, the security posture of an enterprise is only as strong as its ability to swiftly and accurately deploy solutions against identified weaknesses. Let's make effective automation an integral part of our cybersecurity defenses, for Patch Tuesday and every day in between.
We provides a 100% CloudNative IT Endpoint operations platform for modern organizations. As a comprehensive EndPointManagement Platform, it has advanced SoftwareManagement for PatchManagement, Adding, Removing, and Updating Software, Changing and Configure Settings along with PolicyManagement on any device or operating system located anywhere in the world and at any time. With the push of a button, ITAdministartors can fix CriticalVulnerabilities faster, slash cost and complexity, and win back hours in the day.If you want to know more kindly Click here

